October 10, 2014
Besides being the most admired place for social networking, Facebook is a website where people share most of their personal information such as photos, likes, habits, places they visited and even the place they are at the present moment. Therefore, it is extremely important to keep your Facebook account secure in order to prevent any misuse/ account hacking.
Here are some tips to keep your Facebook account secure:
- Create a strong password: Although it is the most basic advice to be given, but most people do not always follow it. Not just for Facebook, it is advised to keep a strong password for all the websites you use. Avoid using simple password like names, date of births, and successive alphabets or numbers. Instead, use a combination of uppercase and lowercase letters, numbers and symbols to make it bit complex. To change your existing password, click on Account Settings> General> Password
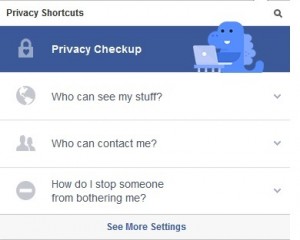
- Customize your privacy settings: You would not want everyone to view your personal stuff that you or your friends post on Facebook. In order to restrict people, you should choose appropriate privacy settings for your account. For that, you need to click on the padlock icon on the extreme right in the top toolbar, click on ‘Who can see my stuff’ and choose your preference from the drop down menu. It is recommended to you limit your privacy to ‘friends’ or ‘friends of friends.’
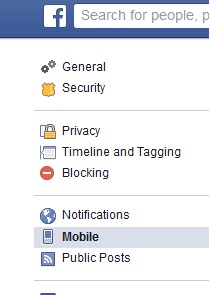
- Confirm Mobile Number: This will help you to reactivate your Facebook account in case you forget your password. To enter your mobile number, go to Account Settings> Mobile> Add a Phone. After this, you will receive a confirmation code on your mobile which you have to enter in the given column. Now, you have your mobile phone registered with Facebook.
- Setup login notifications: You can set up notification alert if anyone tries to access your account from an unknown device. This is an easy way to prevent unauthorized use of your Facebook account. To do this, go to Account Settings > Security > Login Notifications. From here, you can choose either to receive an email or a text message notification for any unapproved login.
- Always log out: Whether it is a public computer or a personal device, make it a habit to log out of your account after every session.
By putting these simple tips into practice, you can be assured of your Facebook account being safe and secure.