Agile, Kanban, Scrum, and Extreme Programming (XP) are foundational pillars within the software development landscape, each presenting unique philosophies and practices.
Significance of Methodology Selection
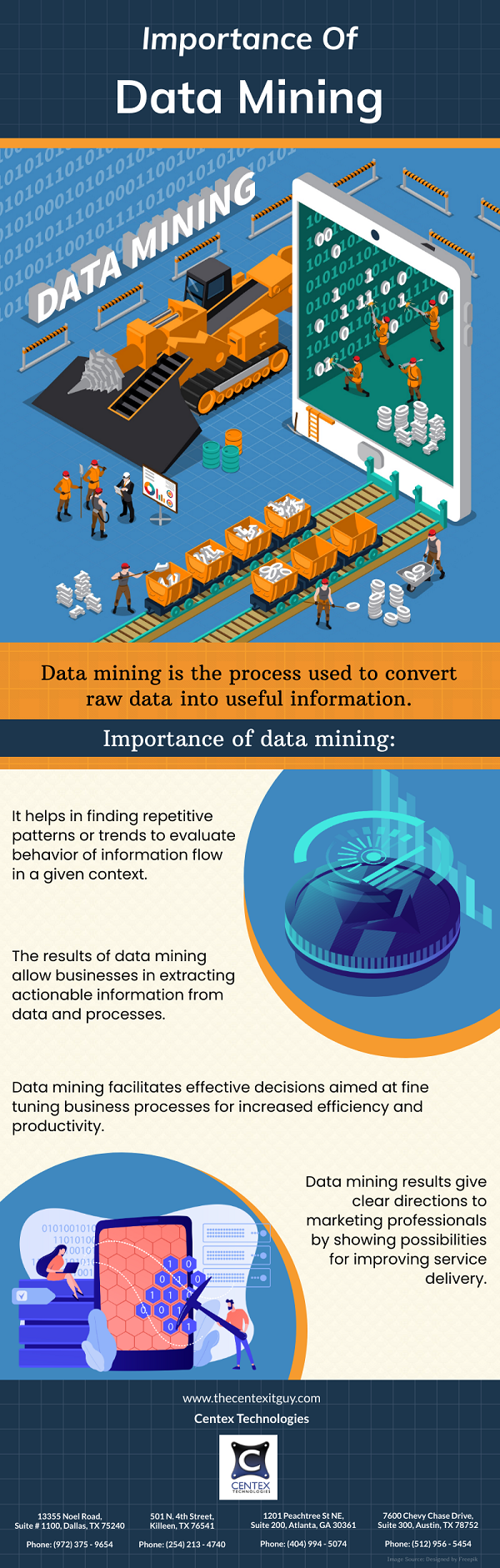
Beyond code creation, software development demands structure, efficiency, and adaptability. The chosen methodology molds the path of projects from conception to deployment. It determines how teams navigate changes, collaborate, and steer towards delivering products that meet both client expectations and market standards.
A well-suited methodology aligns teams, streamlines processes, and empowers flexibility to tackle evolving requirements and market demands. It fosters innovation, enhances communication, and ensures the end product is not just functional but also aligned with customer needs.
Introduction to Agile, Kanban, Scrum, and XP
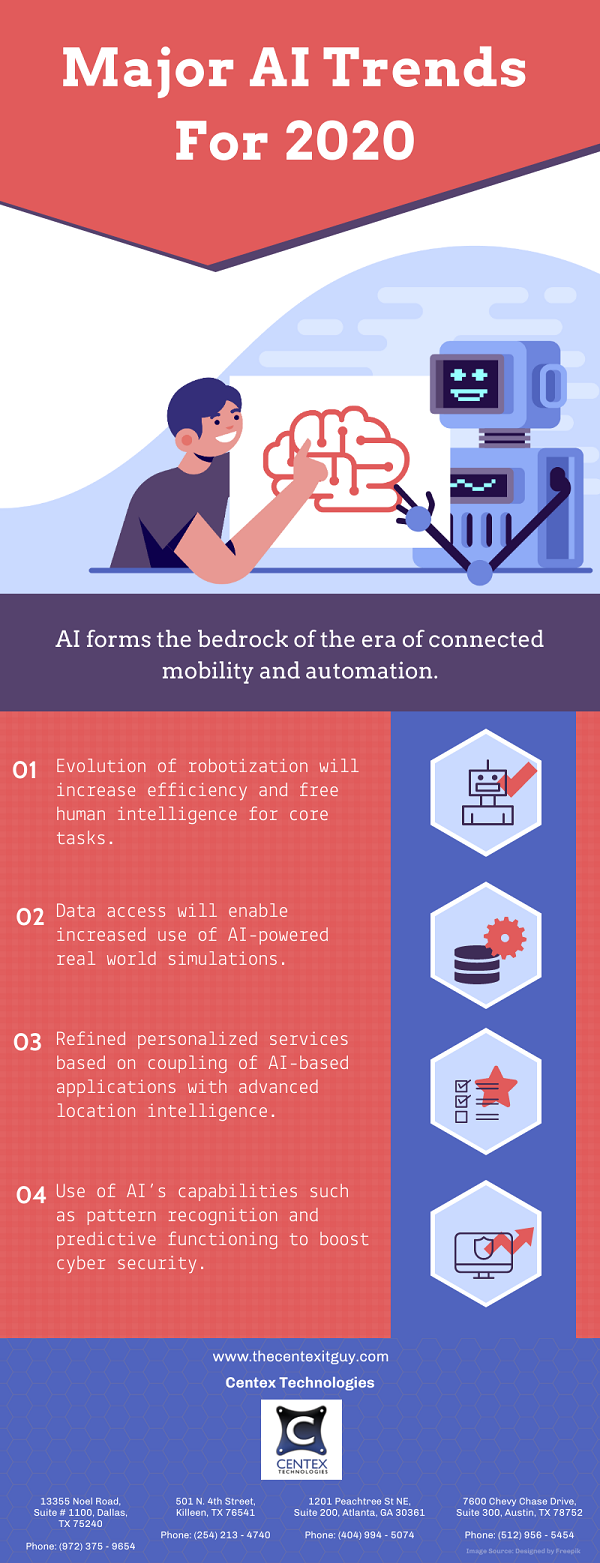
Agile revolves around adaptability and collaboration, emphasizing iterative development and quick responses to change. It champions flexibility and incremental deliveries.
Kanban thrives on visualizing workflows, managing work through limiting tasks and optimizing flow. It focuses on smooth workflow maintenance.
Scrum operates in defined sprints, fostering self-organizing teams to deliver high value within fixed durations. Transparency, inspection, and adaptation are its cornerstones.
Extreme Programming (XP) advocates for high-quality code through practices like pair programming and continuous feedback loops, prioritizing customer satisfaction and adaptable planning.
Each methodology offers a tailored set of principles, practices, and frameworks designed to address specific challenges within the software development lifecycle. Understanding their nuances is pivotal in selecting the most fitting methodology for a project’s unique needs and objectives.
Comparative Analysis of Methodologies
Agile flexes to changing requirements, emphasizing customer collaboration and iterative development. However, its adaptability might sometimes result in ambiguous project scopes, requiring high stakeholder involvement.
Kanban excels in visual workflow management and continual delivery. Yet, its flexible structure might not suit complex projects with fixed deadlines due to its less defined nature.
Scrum ensures clear roles and fixed-length sprints for iterative progress and feedback. Nevertheless, its rigidity in predefined roles might pose challenges in handling mid-sprint changes.
XP maintains high-quality code through practices like pair programming and customer-centric rapid feedback loops. However, it demands significant discipline and might face scalability challenges in larger projects.
Choosing the Most Suitable Methodology
- Project Assessment: Conduct a comprehensive analysis of project requirements, understanding the scope, complexity, and flexibility needed. This assessment lays the foundation for choosing the most suitable methodology.
- Team Dynamics Evaluation: Assess team capabilities, preferences, and their adaptability to various methodologies. Consider the team’s experience, expertise, and comfort with different working structures.
- Company Culture Alignment: Align the chosen methodology with the prevailing company culture. Ensure it resonates with the organization’s values, objectives, and existing practices.
- Flexibility and Adaptability: Consider the level of flexibility required in managing changes and evolving requirements throughout the project lifecycle. Determine the adaptability of the methodology to accommodate unforeseen alterations.
- Project Constraints: Evaluate any specific constraints such as time, budget, or regulatory requirements. Some methodologies might better suit fixed deadlines or budgetary restrictions than others.
Methodology Evaluation and Adoption
- Pilot Projects or Prototyping: Consider running small-scale pilot projects or prototypes using different methodologies. This allows for real-world evaluation of their effectiveness in your specific project environment.
- Team Involvement and Training: Involve the team in the evaluation process to gather diverse perspectives and insights. Provide adequate training and resources for the selected methodology to ensure smooth adoption.
- Continuous Evaluation and Feedback Loops: Establish feedback mechanisms to evaluate the chosen methodology’s performance continuously. Adapt and iterate on the methodology based on ongoing feedback for continuous improvement.
- Gradual Adoption: Implement the methodology gradually rather than abruptly changing established processes. Start with smaller projects or teams to test the feasibility and make adjustments before full-scale adoption.
- Documentation and Communication: Document the selected methodology’s processes, roles, and responsibilities clearly. Communicate these changes effectively across the team to ensure everyone understands and embraces the new approach.
Explore advanced software development methodologies and processes with Centex Technologies. Contact at Killeen (254) 213 – 4740, Dallas (972) 375 – 9654, Atlanta (404) 994 – 5074, and Austin (512) 956 – 5454 for more information.