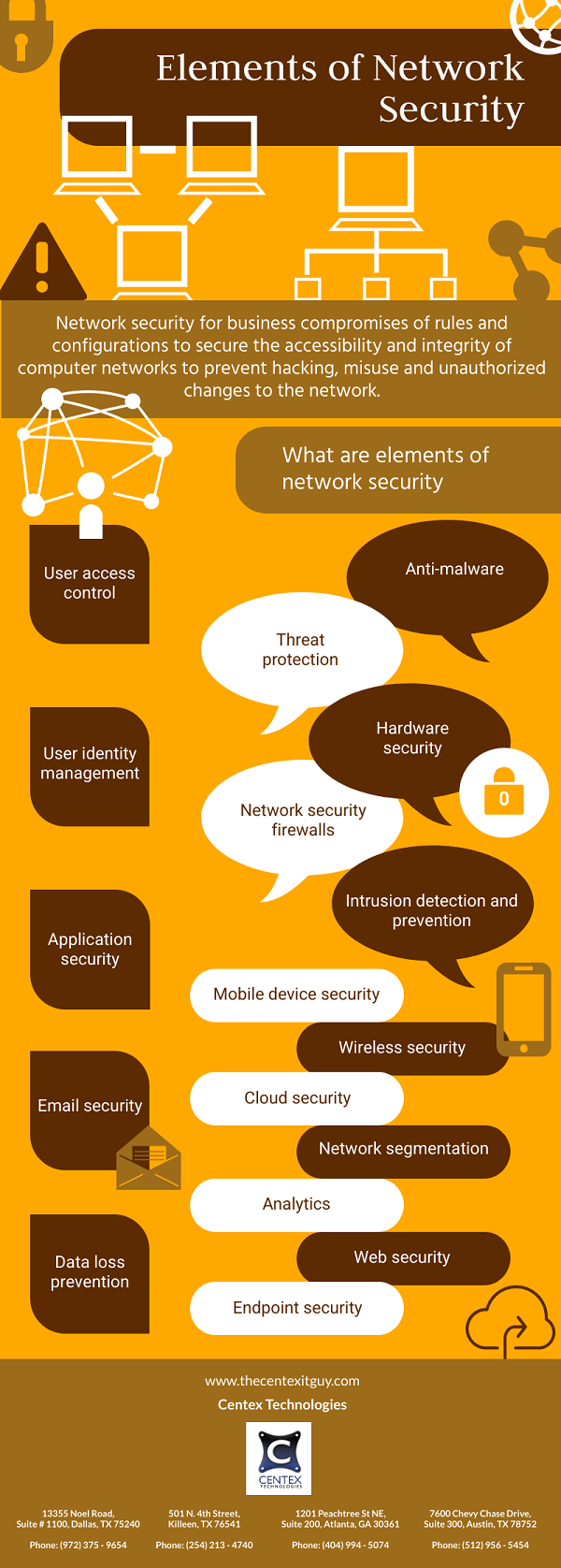
As businesses undergo a change driven by digitalization, many cybersecurity challenges come to the forefront, necessitating strategic attention and innovative solutions. Some of the cybersecurity challenges that need to be addressed while planning digital transformation for an organization are:
Multiple Integrations: Digital transformation involves the thorough assimilation of digital technologies across all facets of an organization, fundamentally changing its operational methods and value delivery. From cloud computing and IoT to AI and automation, the digital frontier offers a wealth of opportunities. However, with innovation comes vulnerability, and cybersecurity must evolve to address the ensuing challenges.
Advanced Persistent Threats (APTs): As organizations embrace digital technologies, they become lucrative targets for Advanced Persistent Threats (APTs). These sophisticated and stealthy cyberattacks aim at unauthorized access, data exfiltration, and long-term infiltration of systems. Digital transformation expands the attack surface, necessitating robust defenses against APTs.
Evolving Threat Landscape: The digital transformation journey is characterized by an ever-evolving threat landscape. Cybercriminals continually adapt and refine their tactics, exploiting vulnerabilities in emerging technologies. Staying ahead of these threats requires proactive cybersecurity measures that anticipate and mitigate potential risks.
Cloud Security Concerns: The widespread adoption of cloud computing is a cornerstone of digital transformation. However, it introduces a unique set of cybersecurity challenges. Issues such as data breaches, misconfigured cloud settings, and unauthorized access pose threats to sensitive information stored in the cloud. Ensuring robust cloud security protocols is imperative for safeguarding digital assets.
Insider Threats in a Digitally Transformed Environment: As organizations digitize their operations, the risk of insider threats amplifies. Employees or third-party entities with access to sensitive information may inadvertently or maliciously compromise security. Effective identity and access management, coupled with continuous monitoring, are crucial to detect and mitigate insider threats.
Integrating IoT Safely: The Internet of Things (IoT) plays a pivotal role in digital transformation, connecting devices and systems for enhanced efficiency. However, the proliferation of IoT devices introduces a multitude of security concerns. Vulnerable devices can act as entry points for cyberattacks, underscoring the importance of having strong security frameworks for IoT.
Data Privacy and Compliance Challenges: As organizations digitize, they accumulate vast amounts of data, raising concerns about privacy and regulatory compliance. Adhering to data protection laws and ensuring secure data handling practices become intricate challenges in the digital landscape. Non-compliance can result in severe consequences, emphasizing the importance of robust cybersecurity policies.
Securing Remote Work Environments: The rise of remote work, accelerated by digital transformation, introduces new dimensions to cybersecurity. Securing remote endpoints, managing access controls, and ensuring secure communication channels are critical aspects of protecting a distributed workforce. Organizations must adapt their cybersecurity strategies to the evolving nature of remote work.
Threats to Artificial Intelligence (AI) and Automation: AI and automation are key drivers of digital transformation, streamlining processes and enhancing decision-making. However, these technologies are not immune to cybersecurity threats. Adversarial attacks on AI models, manipulation of automated processes, and unauthorized access to AI algorithms pose unique challenges that demand innovative security solutions.
Budgetary Constraints and Resource Allocation: Cybersecurity in the era of digital transformation requires substantial investments. Many organizations, especially smaller ones, may face budgetary constraints in implementing comprehensive security measures. Striking a balance between cost-effective cybersecurity solutions and robust protection is an ongoing challenge.
The Human Factor: Amid intricate technological challenges, the human element continues to be a crucial aspect of cybersecurity challenges. Phishing attacks, social engineering, and inadequate cybersecurity awareness among employees contribute to vulnerabilities. A holistic cybersecurity approach should encompass comprehensive training programs and awareness initiatives.
Centex Technologies offers comprehensive digitization solutions for businesses, encompassing thorough planning, strategic implementation, and rigorous testing across various levels to provide efficient and secure operations. For further details, please feel free to call Killeen (254) 213 – 4740, Dallas (972) 375 – 9654, Atlanta (404) 994 – 5074, and Austin (512) 956 – 5454.