Free Wi-Fi access sites found at restaurants, airports, cafes, hotels, bookstores, and even odd retail outlets are usually frequented by people to use their devices or to connect with internet. However, this liberty comes with a cost, and few people are aware of the dangers of using public WiFi. Learning how to defend against the risks that come with utilizing such sites can go a long way toward keeping data on devices safe and secure.
Security Challenges of using a Public WiFi
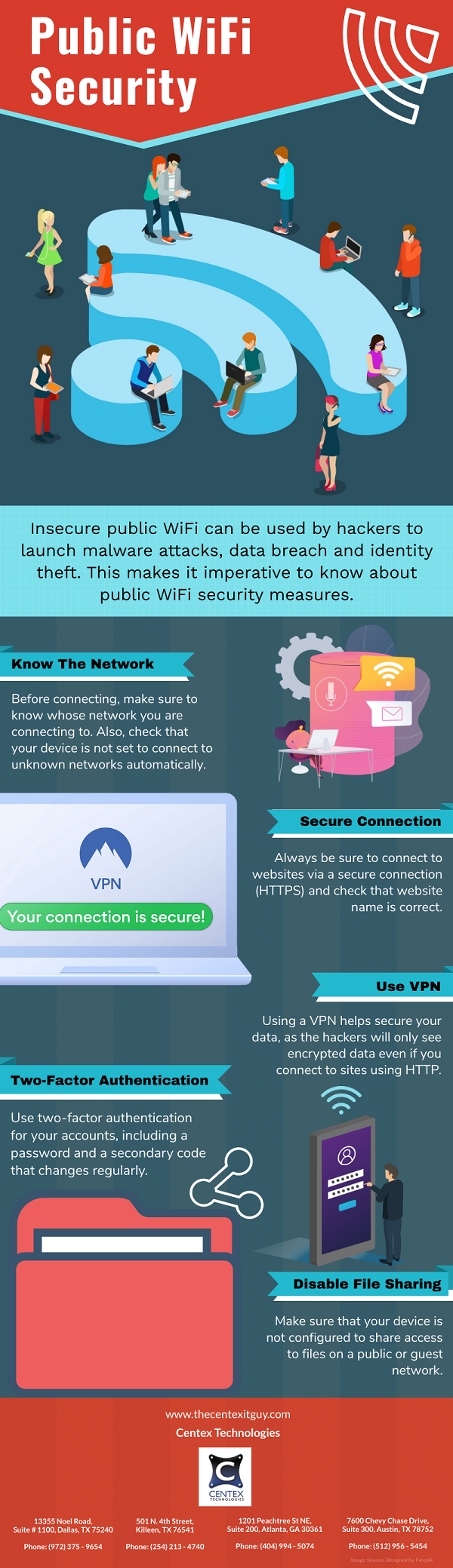
The lack of authentication required to establish a network connection makes free WiFi hotspots desirable to users and particularly enticing to hackers. This gives the hackers a fantastic opportunity to acquire full access to unsecured devices on the same network. Instead of communicating directly with the hotspot, you may end up providing your information to the hacker, who may then pass it on.
While working in a free Wi-Fi arrangement, the hacker may have access to every piece of information you send out on the Internet. While using free Wi-Fi, sensitive information such as emails, credit cards, and even security passwords might be exposed. An unencrypted WiFi connection can also be used by hackers to propagate malware. A hacker can swiftly infect a machine with contaminated software if users share data across a network.
Some of the infamous security challenges users face using a Public WiFi: –
- Compromised Personal Information such as Login credentials, Financial information, Personal data, Pictures, etc.
- Advanced cyber-attacks on individuals’ devices, businesses, automobiles, smart gadgets, etc.
- MitM (Man-In-The-Middle) attacks to breach the privacy of communication.
- Network connections using weak or no secure encryption mechanisms.
- Sniffing and intercepting the network packets i.e. the communication channels breaching confidentiality.
- Distributing and injecting malware into devices and network systems.
- Hijacking the devices and networks using Public WiFi to connect to the internet.
How to prevent or reduce the damage arising from using Public WiFi
A. Transport-level SSL Security
Even if users do not have access to a VPN application for daily Internet browsing, they can still secure their communications. For those websites, being visited regularly or that need one to input credentials, “Always Use HTTPS” option should be selected. Hackers are aware of how people reuse passwords and thus a user’s login and password for some random forum might be the same as the bank or workplace network, which they may exploit.
B. Keep the Public Sharing option Off
Users are advised not to disclose anything when using the Internet in a public area. They can deactivate sharing on WiFi using the system settings the first time they join an unprotected network.
C. Connecting to the Internet using VPNs
When connecting to a business network through an insecure network, such as a WiFi hotspot, a VPN (Virtual Private Network) connection is essential. Even if a hacker manages to get in the middle of the encrypted connection, the data is heavily secured. Because most hackers are looking for a quick buck, they are more likely to throw away encrypted stolen data rather than decode it.
D. Turn Off the WiFi when not in need
Even if users are not connected to a network, WiFi technology still communicates between any networks within their range. There are security mechanisms in place to keep this tiny communication from compromising the users’ devices. It is strongly advised to keep the WiFi turned off if users are only working on a Word or Excel document or any offline application on their devices.
E. Follow the security guidelines provided by the Security Vendors
Even those who take all feasible measures when using public WiFi can occasionally encounter problems. Hence, it is critical to have a good Internet security program installed on the devices. These programs can scan files for malware regularly. They can also scan new files as and when they are downloaded. The best consumer security software often includes business protection features, allowing users to safeguard themselves while simultaneously protecting their servers at work.
There will come a point in every business traveler’s life when the only connection available is an insecure, free public WiFi hotspot. Being equipped with the right security solutions will help the user avoid being a victim of a cybercrime.
Centex Technologies provide state-of-the-art cybersecurity and internet security solutions to businesses. To know more, contact Centex Technologies at Killeen (254) 213-4740, Dallas (972) 375-9654, Atlanta (404) 994-5074, and Austin (512) 956-5454.