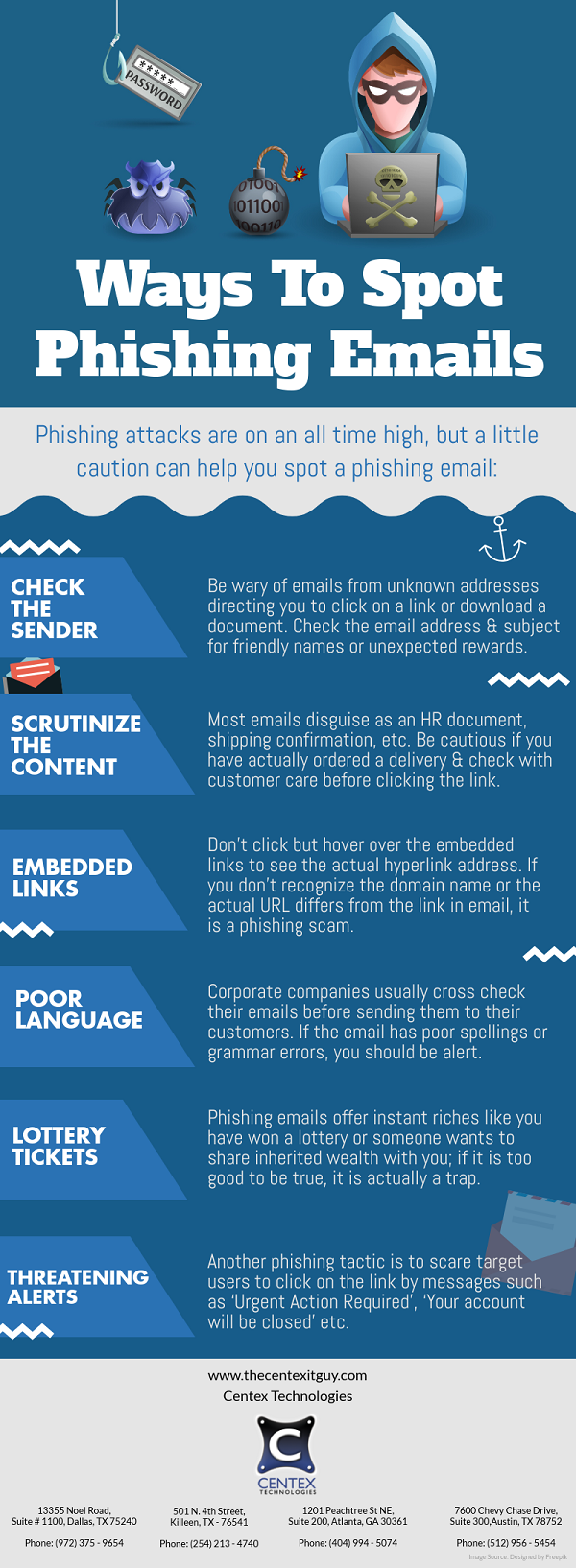
PDF Version: Ways To Spot Phishing Emails
Robotic process automation (RPA) involves using a software that is programmed to do basic tasks just as humans do. It uses artificial intelligence & machine learning to handle high-volume & repetitive tasks that were originally performed by humans. The tasks may vary from solving queries, making calculations, record maintenance, sending receipt messages, updating a spreadsheet, etc. The RPA software is basically designed to reduce the burden of simple routine tasks.
Applications Of RPA
- Customer Service: RPA software helps in improving overall experience of customers by automating contact center tasks to provide better service.
- Accounting: RPA can be used to perform certain accounting tasks such as general accounting, transactional reporting, budgeting, etc. This helps in reducing human effort as well as saving time.
- Healthcare: RPA solutions can be used to handle medical records of patients, provide previous medical history, customer support, hospital account management & billing.
- Human Resource: Tasks such as filing & updating employee information, on-boarding & off-boarding, etc. can be handled by a software bot.
- Supply Chain Management: From procurement, order processing, monitoring inventory levels to shipment tracking, RPA can also be used for managing numerous tasks performed in the supply chain.
What To Look For In A RPA Software?
- Speed
- Scalability
- Reliability
- Simplicity
- Intelligence
RPA Implementation Methodology
- Planning: The first step is to plan and list the tasks you want to automate.
- Development: In this step, the RPA software is developed as per the needs specified in the planning phase.
- Testing: The software is pre-tested to identify & correct the defects.
- Support & Maintenance: Support is needed even after a software goes live.
Benefits Of Resorting To RPA
- Cost Saving: Robotic process automation helps in significantly reducing costs as tasks that were earlier done manually can be automated using RPA software. This improves the overall process performance and revenues of the business.
- More Accuracy: Employees need to be very careful while performing a task because there are chances of inaccuracy. However, RPA automates the work which eliminates human errors & mistakes. This in turn, improves the quality & efficiency of work performed.
- Saves Time: Robots can perform tasks at a higher speed as compared to human workforce. This helps in reducing the time taken to perform a task.
- Gathering Insights: RPA software has the ability to gather, organize, analyze and provide valuable data insights to ease the process of planning & decision making.
- Simple: Training an employee consumes time whereas RPA solutions are programmed as per need of the business. It is very easy & flexible to operate.
For more information, call Centex Technologies at (254) 213-4740.
Big data has positively impacted numerous industries including retail sector. It provides a competitive edge to businesses to stay ahead of time. As per a report of Statista, decentralized general-merchandise retailers who use big data to create performance group clusters, saw an approximate increase of 3-4% in their sales. Big data analytics help the companies understand customer’s shopping trends, get meaningful data insights, plan marketing strategies, etc. which can help them improve their bottom line figures.
Let us discuss in detail how big data impacts retail sector:
- Generating Recommendations: Big data analytics enable businesses to predict customer buying behavior based on their purchase history. This helps the retailers in understanding their product preferences and plan accordingly. Also, machine learning models enable retailers to generate accurate recommendations for the customers.
- Forecasting Market Trends: Customer’s demographic information and other economic indicators can be used to forecast market demands.
- Strategic Decision Making: Businesses can consolidate data & generate information for making strategic & informed decisions.
- Personalized Marketing: Big data enables retailers to perform one-to-one marketing and reach out to the target customer at the right place and at the right time.
- Identifying Valuable Customers: One major benefit of big data analytics is that it helps the retailers to identify and focus on valuable customers. Thus, businesses can offer them additional discounts for better engagement, enhancing customer loyalty, etc. by capitalizing on the data insights.
- Right Pricing: Earlier, retailers used to reduce the price of their products at the end of a buying season. However, big data analytics help the businesses in determining when the demand starts decreasing to gradually decrease the prices, thus maximizing revenues.
- Enhancing Customer Experience: Big data analytics helps in anticipating buyer’s preferences which leads to a seamless customer experience.
- Designing In-Store Marketing Tactics: Big data enables retailers to adjust & design in-store marketing strategies. It considers factors like foot traffic, in-store checkout & wait time, etc. to serve their customers better as well increase business’s revenue.
- Utilizing Market Basket Analysis: Big data tools like Hadoop are used to conduct market basket analysis. It helps retailers to analyze the purchase history to understand the combination of products that are usually bought together by their customers.
Every individual has a digital footprint and big data is used to gather insights about an individual’s choices to form reasonable patterns out of it. Big data can be used at every step of retail process i.e. from recognizing target customers, studying their preferences to identifying market demand. Thus, big data analytics play a very important role in retail marketing.
For more information on Big Data and its application, call Centex Technologies at (254) 213-4740.
Smartphones are coming up with new features every day, touch ID scan being one of them. This feature allows you to unlock your phone, approve a purchase or protect access to applications using a fingerprint or face scan instantly. It is highly beneficial as it prevents people from accessing your critical apps & personal information if they happen to lay hands on your unlocked device.
However, off lately cybercriminals have come up with touch ID scams to exploit users and steal away their confidential information.
How Does The Scam Work?
Since touch id scan is a convenient option, people are using it for more than just unlocking the phone. Nowadays, touch ID is being used for authentication on various apps. However, once you press your finger against the home button, there is generally no additional prompt to confirm whether you want to purchase the app or not.
The scam apps often pose as health assistants and invite users to use a touch ID to track calories, heart rate, etc. When you scan your fingerprint, an in-app purchase pop-up appears on the screen. Consequently, the screen is dimmed to make it hard to see the prompt. Once authorized, it usually charges you somewhere between $90 to $120 and the user is victimized by a touch ID scam.
How To Avoid Falling Prey To A Touch ID Scam
- Double Check If It Looks Suspicious: If any app functions in a way other than normal, then be wary of it and avoid it altogether. The app might ask you to hold down your finger longer than usual, register your fingerprint in different ways, might not support fingerprints that you have saved with android/iOS or ask you to do a fingerprint scan numerous times to authenticate.
- Check Reviews: Make sure that you read the reviews before downloading a new app. To some extent, this may help you know if the app is legitimate or not. However, if you decide to download it, then stay a little cautious and report it if you find any problem.
- Disable Fingerprint Or Face Authentication For Purchases: The best way to stay safe is to disable fingerprint as well as face authentication for purchases. Even though you will have to type the password manually, it will give you extra time to consider if you wish to purchase an app or not. This is unlike fingerprint authentication where pressing the home button prompts the purchase.
- Prefer Trusted Developers: When downloading an app, it is always preferable to buy the one that has been developed by trusted companies. Reputed apps usually have thousands of downloads and their developers have a significant online presence on websites & social media.
For more information, call Centex Technologies at (254) 213-4740.
Every industry makes use of internet to ease its operations. It helps in increasing efficiency of the business; however, it also serves as a gateway to cyberattacks. Cyber insurance does not guarantee protection from a cybercrime, but it ensures financial stability if such an event occurs. Thus, getting a cyber insurance is a way to transfer risks.
What Is Cyber Insurance?
Reports of high profile cyber risks have driven the need for cyber insurance to financially protect businesses from cybercrimes. Given the soaring rates of cyber-crimes, gross written premiums for cyber insurance will be $7.5 billion by 2020; as estimated by PwC.
Also referred to as cyber risk insurance or cyber liability insurance, the primary aim of cyber insurance is to help organizations mitigate risks by compensating for losses arising due to cyber related security breaches. Cyber insurance is meant to protect businesses from internet based risks such as data breaches, network security breaches, loss of privacy, theft of intellectual property, etc.
However, the cyber insurer does a thorough evaluation of the security systems & procedures of the organization before providing a cyber insurance.
What Does Cyber Insurance Cover?
It usually covers first party expenses as well as third party claims. Following are some expenses that are covered by cyber insurance:
- Business Losses: The insurance policy might cover monetary loss caused due to business interruption, data loss recovery, network downtime, cost incurred on re-establishing the reputation, etc.
- Privacy & Notifications: It covers liability arising due to loss of private & confidential information of the customers, employees, clients and other parties. It also includes the cost of notifying the third parties affected by the data breach as mandated by laws of the state.
- Investigation: A forensic investigation is conducted to determine the cause of data breach. It is vital to know the source of breach to infer the way to repair damage. Also, it helps in ascertaining preventive measures needed to avoid any cyber breach in future.
- Extortion & Lawsuits: Cyber insurance covers the legal expenses arising due to release of confidential information, legal settlements, regulatory fines, etc. Costs of cyber extortion such as those arising from a ransomware are also included in it.
- Data Restoration: This coverage provides for the cost of restoring the lost data.
Things To Consider Before Taking A Cyber Insurance Policy:
- Risk of data breach
- Financial resources available
- Coverage options available
- Deductibles
Thus, cyber insurance provides businesses a smooth funding for recovery from major losses. However, the first step is to create a cyber risk profile for your company. List down all the expenses including first party & third party costs that you wish to get a coverage for.
For more information about cyber insurance, call Centex Technologies at (254) 213-4740.