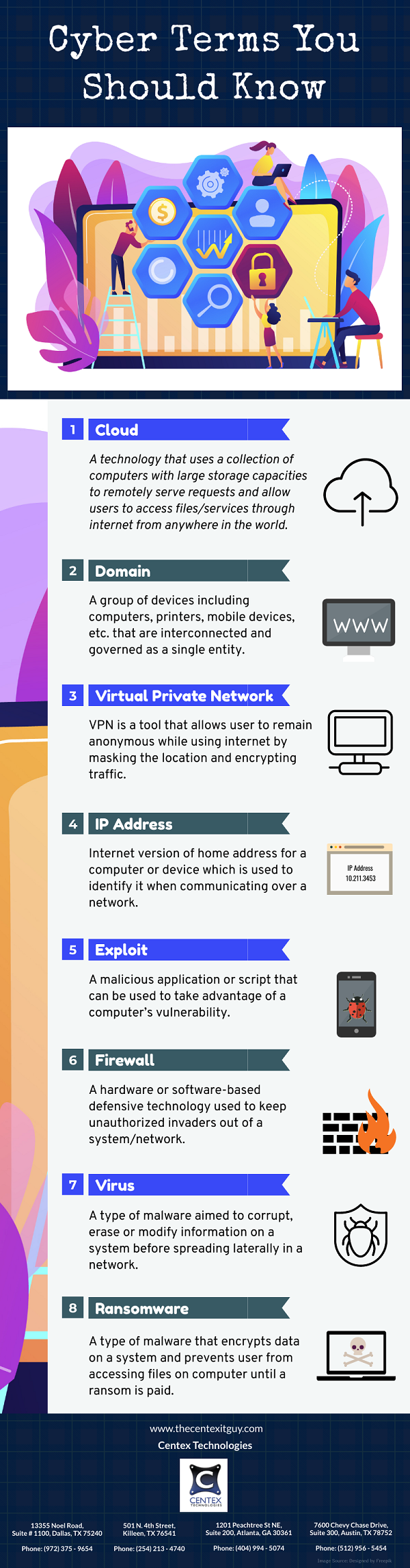
 PDF Version: Cyber-Terms-You-Should-Know
PDF Version: Cyber-Terms-You-Should-Know
An insider threat is a type of malicious activity against an organization that comes from users having authorized access to the network, databases, or applications of the organization. These users can be current employees, former employees, or third parties like partners, contractors, temporary workers, etc. This type of threats also includes users who unintentionally cause harm to the business.
Understanding insider threats is highly important because the frequency of insider threats has increased. As per “2020 Cost of Insider Threats: Global Report”, 60% of organizations had more than 30 insider-related threats per year and number of insider threats has increased by 47% in two years.
Types Of Insider Threats:
Malicious Insider: This type of threat includes an employee or partner who purposely tries to steal information or disrupt operations.
Negligent Insider: This is an employee who puts the organization security at risk by not following proper IT procedures. For example –
- An employee who left his computer logged in and unattended.
- An administrator who did not change a default password.
- An IT professional who did not install a security patch.
Compromised Insider: An example of a compromised insider is an employee whose computer has been infected with malware via a phishing scam or compromised downloads. The compromised machine is used by cyber criminals for stealing data, infecting other systems, etc.
How Are Employees Compromised?
Different means that can be used to compromise an insider are:
- Phishing – The target employee is contacted via email or text to bait the individual into providing sensitive information.
- Malware Infection – The machine is infected with malicious software to infiltrate the system and steal sensitive information or user credentials.
- Credential Theft – Cyber criminals adopt techniques such as phishing, malware, bogus calls, and social engineering to trick users into providing username and password.
- Pass-the-Hash – This is similar to password theft attack but relies on stealing and reusing password hash values rather than actual plain text password.
Ways To Prepare Against Insider Threats
Following steps can be used to be prepared against insider threats:
- Employee Training
- Coordinate IT Security & HR
- Build A Threat Hunting Team
- Employ User Behavioral Analytics
Centex Technologies offers assistance to businesses in ensuring security from insider threats. For more information on cybersecurity solutions for businesses, contact Centex Technologies at (254) 213 – 4740.
Cloud computing is a vast term that covers a wide range of technology resources that are delivered “as-a-service” via an internet connection. The cloud services include software-as-a-Service (SaaS), platform-as-a-service (PaaS), and infrastructure-as-a-service (IaaS). All these cloud computing models provide a different level of service, control, and responsibility.
When switching to a cloud computing model, business organizations need to be aware of the following cloud computing challenges:
- Potential Loss Or Theft Of Intellectual Property: IP represents competitive advantages for a business, so a loss of IP may have a tangible impact on the business’s market share. Fraudsters may use this IP information to create fake products and cheaper processes since they don’t cover research & development costs.
- Regulatory Compliance Violations: Cloud computing service providers may not meet the strict regulatory compliance standards of the industry. It can lead to compliance violations for businesses availing these services.
- Reduced Visibility Of Cloud Environment: Some Cloud Service Providers do not provide visibility into the cloud environment. This problem is more intense in SaaS solutions because PaaS and IaaS solutions offer more visibility. After all, in these cases, users are expected to do their configuration and management for the cloud environment.
- Lateral Attack Spread: If defense-in-depth controls of a cloud environment are not strong enough, it can be easier for an attacker to spread from one workload on the cloud to the next. Thus, multiple databases or apps can be compromised quickly during a breach.
- Increased Complexity Of Security: Businesses that work with multiple cloud service providers have to face several different complicated cloud security processes. For example, one CSP may require multi-factor authentication using text messages, while another CSP may use a different authentication method. It increases process complexity making it difficult for users to access various cloud solutions in their day-to-day workflows.
Solutions To Cloud Computing Security Challenges
- Limit Cloud Computing Vendors: Different Cloud Service Providers may have different security tools and processes, making it difficult for businesses to manage their cloud solutions. This challenge can be handled by trying to limit the cloud computing vendors. Companies should try to source as many cloud solutions from a single vendor as possible.
- Verify Your Access To Information: Visibility into the cloud environment is vital for ensuring cybersecurity. So, verify the level of access to information that Cloud Service Provider would offer. With greater visibility into the cloud environment, businesses can more easily track and control security.
- Verify Security SLAs: Verifying security SLAs (Service Level Agreements) before signing an agreement with CSP helps to ensure that the service provider will meet the industry’s cybersecurity standards and protect the business from extended service disruptions.
- Consult A Cybersecurity Expert: Get assistance from cybersecurity experts before switching to the cloud computing model.
We, at Centex Technologies, help businesses in switching to cloud computing. We offer IT consulting services for educating businesses on their cloud computing requirements and ensuring cybersecurity. For more details on challenges & solutions related to cloud computing security, contact Centex Technologies at (254) 213 – 4740.
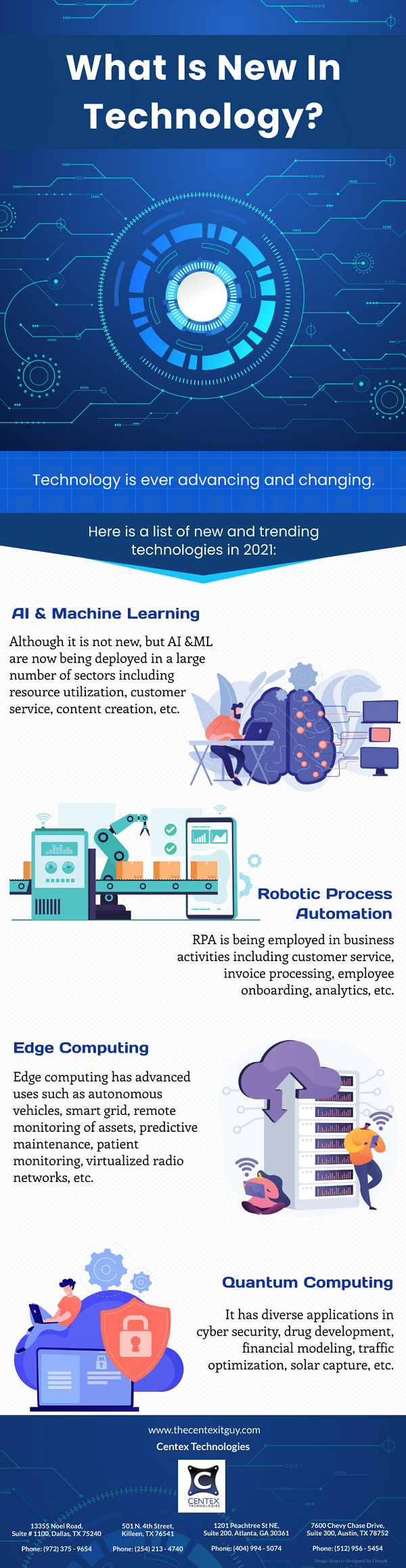 PDF Version: What-Is-New-In-Technology
PDF Version: What-Is-New-In-Technology
Server infrastructure helps organizations in managing most of their IT functions which includes data storage, website hosting, emails, and software applications. Although a number of organizations have shifted to cloud servers, some organizations still have in-house servers or hybrid server infrastructure. In order to ensure efficiency of in-house and hybrid server infrastructures, organizations need to undertake effective server management.
Goals Of Server Management
An effective server management strategy should focus on three primary goals:
- Work towards minimizing or eliminating server slowdowns and downtime.
- Building secure server environment.
- Ensuring that the server continues to meet the needs of the organization as it grows.
Server Management Basics
Hardware Management: This is the first step towards server management. Some important hardware elements that need continuous monitoring are CPU (Central Processing Unit), RAM (Random Access Memory), and Hard Drive. Other hardware management elements include CPU temperature and operating environment. An important point of consideration while choosing server hardware is to keep in mind the required server specifications. Make sure to choose excess storage and processing capacity as it would allow easy up-scaling of server, when required.
Software Management: In order to ensure effective software management, it is important to understand the software dependencies in the server infrastructure. A suggested approach is to employ basic best practices along with application management. The software, firmware and operating systems should be regularly updated for performance and security. Outdated versions may lead to poor performance and also create vulnerabilities that may be exploited by cyber criminals to infect organization’s network and server. Software that are no longer used should also be removed.
Security: Maintaining secure network is an important component of server management. The security policies may vary depending upon industry type and individual organization’s needs. However, some common server security solutions include-
- Installing and regularly updating antivirus software.
- Enable firewall
- Use access control software such as Kisi, ISONAS, ADT, NetMotion Mobility, etc.
- Employ data encryption
- Implement SIEM tools such as SolarWinds Security Event Manager, Micro Focus ArcSight ESM, Splunk Enterprise Security, IBM QRadar, etc.
- Use security logging best practices
Backups: The last step towards effective server management is to take regular backups. Make sure to employ server backup software among other backup solutions. Some examples of popular server backup software are V2 Cloud, Unitrends, Veeam, GoodSync, BackupVault, etc.
We, at Centex Technologies, help businesses in ensuring effective server management by employing customized solutions. For more information, contact Centex Technologies at (254) 213 – 4740.
