February 19, 2014
Facebook has emerged as a one of the favorite mediums for business owners who wish to target a selective audience. Unique ability of Facebook to send promotional messages to users specified by demographics has facilitated Internet marketers to produce better results. You can choose to promote your business based on by age, gender, location and interests of targeted audience. The various effective methods by which you can promote your business on the leading social networking site are listed below:
Facebook Page
Using Facebook page to create a business profile helps highlighting information about business location, schemes, offers, special discounts of an enterprise over the social network. Option of “like” allows users to endorse the business and stay updated with latest developments, news and other activities of business. A dedicated page on Facebook about the business can help build a communication channel between customers and service providers. Thus, answering queries of users and helping them becomes far more convenient. Facebook page also helps in promoting various non-business activities of the company and thereby boosting the brand’s reputation.
Facebook Ads
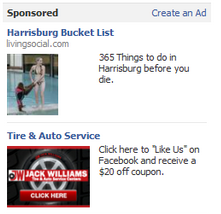 Facebook allows enterprises to create and promote advertizements and showcase them to users according to the demographics. The ad is placed on the right hand side of the webpage. To make the ad more attractive, facebook gives the option to use images along with the text. Besides selecting a set of users based on demographics, you can also pick a particular ad to cater to a particular “group” or “friends of friends” who have already liked your Facebook page.
Facebook allows enterprises to create and promote advertizements and showcase them to users according to the demographics. The ad is placed on the right hand side of the webpage. To make the ad more attractive, facebook gives the option to use images along with the text. Besides selecting a set of users based on demographics, you can also pick a particular ad to cater to a particular “group” or “friends of friends” who have already liked your Facebook page.
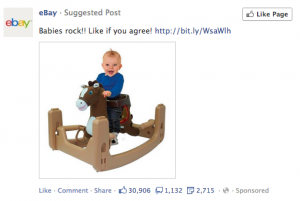
Facebook allows advertizers to post “suggested posts” on news feed of specified users. Sponsored posts help send messages to users.
Though these are the prominent Facebook marketing strategies provided by Facebook, an Internet marketing company well-equipped with knowledge will make use of all the features available to market their clients’ business. Various campaigns can be created and effectively implemented using “share” and “like” features. It is important to upload posts that are not only informative, but can also pledge a viral promotion. Pictures, quotes, videos that appeal to masses serves the cause further of marketing a product or service on Facebook.
We at Centex Technologies provide Facebook marketing services to clients across the globe. For more information call us at – (855) 375-9654