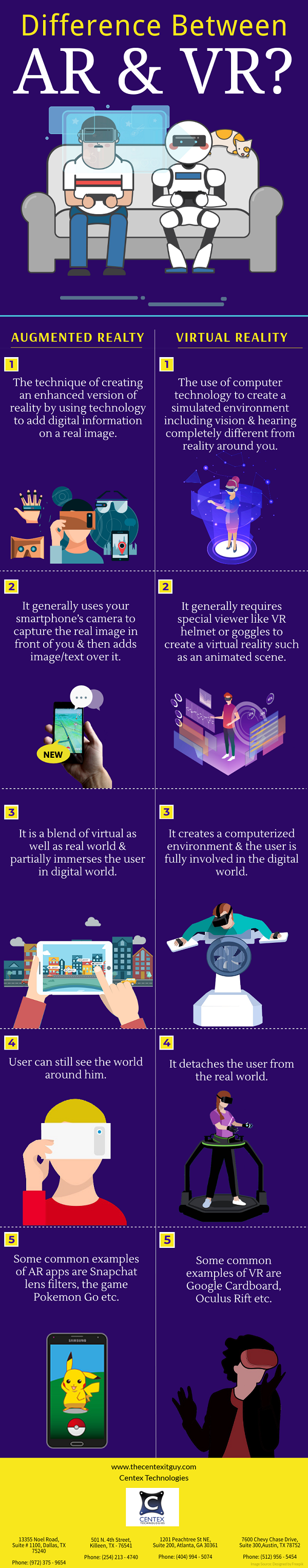
PDF Version: Difference-Between-AR-&-VR
Public cloud is a computing service offered by a third party provider to users. It can be used by anyone who wants to use or purchase the cloud service. Not only does public cloud systems help in saving purchasing costs, but also reduces management & maintenance expenses for hardware & software infrastructure. A distinctive feature of using public cloud service is that many personnel can simultaneously use an application from their respective devices. Although public cloud offers infinite scalability and can be deployed faster, it is advised to take appropriate measures to prevent any security lapse. Below we have discussed certain points that can help in strengthening public cloud security for an enterprise.
- Select The Right Apps For Public Cloud: Businesses use public cloud for all applications. However, it is advisable to diligently scrutinize & avoid using public cloud for mission-critical apps and data.
- Add Security Layers: Since numerous users can access the content from the cloud, so it is essential to protect it. If you fail to secure the apps & data, it gives attackers an open window to attack and get access to restricted data. So, it is always advisable to encrypt the data and keep it protected. You must also add additional authentication layers like passwords & user credentials.
- Access Control: Most organizations are opting for cloud technology as it allows employees to gain an access to data from any geographical location with the help of an active internet connection. However, with the increasing BYOD culture, the risk of data intrusion has also ascended. In a report by Forrester, 80% of security breaches involved privileged credentials. In order to avoid such scenario, it is important to have due control over data access. Make sure that you give password access to trusted employees only and minimize user account privileges. Also, access to any sensitive data stored on cloud should be limited to employees having entitled authority to utilize such data.
- Backup Data: Data stored on public cloud is prone to numerous risks. The best way to avoid any risk is to take regular cloud backups. Having additional copies of data helps in preventing any kind of business loss & minimize business interruption.
- Use Third Party Auditing Services: Organizations should opt for third party auditing services for enhanced security. Businesses can move the applications to public cloud followed by an audit to ensure that the security protocols match the standards promised by cloud service provider. This increases their feasibility and also enables them to move confidential information to the cloud.
- Train Your Staff: Hacking attacks are increasing day by day. To prevent such attacks, it is advisable to train your employees about the working of public cloud. This enhances the security and reduces the chances of data loss.
For more information about Cloud Security, call Centex Technologies at (254) 213-4740.
Endpoint security is a methodology to protect the business network when being accessed by remote devices like smartphones, laptops, tablets & other wireless devices. It includes monitoring their status, software as well as activities.
Nowadays, employees are granted network access through the internet on their mobile devices which increases the need to focus on endpoint security. Enterprises have to work on securing the data available on their employee’s mobile device such that if the device falls into wrong hands, the data still stays protected. Security software such as antivirus, antispyware, firewall, etc. are installed on all endpoint devices as well as network servers.
Why Is It Called Endpoint Security?
Devices connected to the network are called endpoints as they are placed on edge of the network and are used by individuals to perform various tasks. Individuals connect to the central network using these endpoint devices. However, these devices may pose a security threat to the network and the strategy that is employed to secure these endpoints is thus known as endpoint security.
Why Is It Important To Ensure Endpoint Security?
- There has been a significant increase in BYOD culture
- There is a rise in number of employees who work from home
- Increase in security threats via mobile devices
Ways To Implement Endpoint Security
- User Management: Businesses should control the user access to the network. It can be done by setting up password protocols, restricting administrative privileges, usage policies, mobile device management, etc. It should be implemented in such a way that if a user loses his device then the IT team can remotely lock the device to protect the data from being compromised.
- Encryption: Another way to keep the data safe is to implement encryption on endpoints. It is simple yet effective way to prevent the data stored on corporate devices from any risk.
- Antivirus & Malware: In the wake of rising phishing & ransomware attacks, it is mandatory to install antivirus & malware protection software on your mobile devices. This helps in increasing endpoint security.
- Updating & Patching: It is important to keep the devices updated. This is because devices without latest updates & patches are most vulnerable to security breaches.
Often there is a confusion between endpoint security & antivirus, although they differ from each other. The former is much wider than the latter. Antivirus protects the PCs, single or many, depending upon the type of antivirus being deployed. However, in case of endpoint security the whole network is made secure. It provides provisions for application whitelisting, endpoint detection & response, network access control, etc. unlike an antivirus software.
By implementing endpoint security solutions, businesses can exercise greater control on number & types of access points on the network.
For more information about IT security, call Centex Technologies at (254) 213-4740.
A Malware-Bot is a type of malware that exercises control over the infected machine once the infection spreads through the system. It acts according to the instructions given by the master i.e. malware writer. Following are some most commonly asked questions about Malware Botnet:
- What Actions Does A Malware Bot Perform?
A Malware Bot can perform numerous tasks such as-
- Spying & tracking
- Sending spams, hosting command servers, working as proxies & performing other malicious activities
- Accessing corporate resources & hijacking
- Stealing confidential information, documents, credentials, etc.
- Bitcoin mining
- Web browsing
- Do All Malware Bots Perform The Same Actions?
The bot can perform all the above mentioned actions, however there are two types of malware actions that the Malware Bot does not perform, not because it is incapable to do so but because they make little business sense. Following are the two malware actions:
- Actions Which Impend The Machine: A Malware Bot cannot work in a damaged environment. When the software environment is damaged the machine is usually reinstalled, thus removing the bot. So, Malware Bot does not usually perform an action that would restrain it from running on the machine.
- Actions That Reveal The Infection: A bot does not want a user to know about its presence on their machine, which is why it operates stealthily. Thus, it does not resort to activities such as modifying browser setting, popping up dialogue box, etc.
- How Are Botnets Investigated?
When the malware is launched, it reaches the malware researchers sooner or later. They capture it through various channels such as malware spam, honeypots, phishing sites, product reports, etc. Once captured, the malware researchers analyze it in a controlled environment to receive the updates.
- How Is A Botnet Controlled?
It is controlled by a computer or a group of computers running a command & control server (C&C server). The server communicates & sends instructions to the Malware Bot in the format understood by it. The server then performs numerous functions such as instructing the bots to schedule or execute a task, keeping track of number & distribution of bots as well as updating the bots by replacing them with a new type of malware.
- Why Do Botnets Emerge?
The main reason why the malware writers develop, deploy & maintain a botnet is to tap on financial gains.
- How To Prevent A Malware Botnet?
After understanding the working of a malware botnet, let us know how to prevent it:
- Update your operating system regularly.
- Avoid downloading from P2P & file sharing networks.
- Don’t click on suspicious attachments & links.
- Install a good antivirus software.
- Follow good surfing habits.
For more information, call Centex Technologies at (254) 213-4740.