 PDF Version: Comprehensive-Guide-To-MITM-Attack
PDF Version: Comprehensive-Guide-To-MITM-Attack
Tag: man in the middle attack
With advanced methods of cybersecurity attacks and breaches coming into play, business organizations need to be more vigilant in planning their course of action to ensure their safety. This is where the need for cybersecurity strategy & implementation plan arises.
What Is Cybersecurity Strategy & Implementation Plan (CSIP)?
CSIP is a plan that states the steps to be taken for formulation, implementation, testing, and refining an efficient strategy to secure an organization against cybersecurity attacks. The intent of CSIP is to identify & address critical cybersecurity gaps and emerging priorities.
What Are The Objectives Of Cybersecurity Strategy & Implementation Plan?
There are five main objectives of CSIP, namely:
- Prioritized Identification & Protection: This involves analysis of organizational resources to form separate categories of data, information, and resources. These categories are then prioritized based on their value. This helps in identification of high value information & assets that need to be secured immediately. After identification, it is important to understand types of risks against the identified assets such as outsider risks (network breach, phishing, hacking, etc.) or insider threats (rogue employees, unaware employees, compromised flash drives, etc.). The detection of risks makes it easier to define the strategic steps to protect the assets. Test your strategy & refine it. Once top priority information is secured, repeat the process for category of assets at next priority level.
- Timely Detection & Rapid Response: Cyber criminals keep evolving their attacks to disrupt stringent cybersecurity strategies. If not detected timely, these attacks can disrupt the layers of security to reach core network, data center and systems of an organization. So, conduct regular checks and analysis to detect a cybersecurity disruption at its nascent stage and stage a rapid response against it. Also, train the employees to make them capable of spotting a cybersecurity breach.
- Rapid Recovery: Some security breaches may cause damage; however, a rapid recovery can help in containing the widespread of damage. It is important to formulate rapid recovery plan. The plan should include steps to be taken, role of teams & individual employees in recovery, and security checkups to ensure the threat has been nullified.
- Skill Building: Recruit qualified cybersecurity workforce to stay protected. An alternative approach is to seek services of a cybersecurity firm and invest in SaaS applications. Conduct regular trainings to enhance cybersecurity knowledge and skills of all employees. This will help them in staying protected against individual targeting attacks such as phishing.
- Technology: Focus on efficient & effective acquisition and deployment of existing & emerging technology. Make sure all systems and devices are updated with latest software & security patches.
For more information on cybersecurity strategy & implementation plan, contact Centex Technologies at (254) 213 – 4740.
May 30, 2015
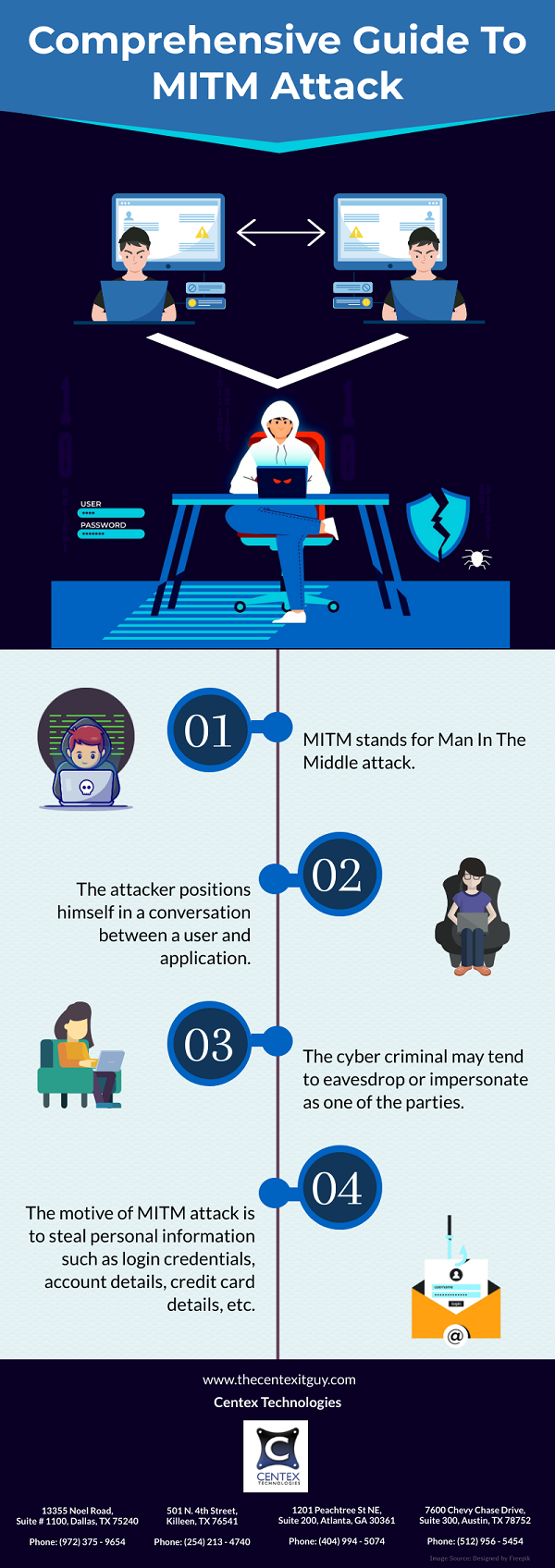
A man-in-the-middle (MITM) attack occurs when an unauthorized user attempts to actively monitor, capture and control the information transmitted between the source and destination computer. The attack may be carried out to simply gain access to the encrypted/unencrypted information or empower the hacker to modify the message before passing it further.
How Does A Man-In-The-Middle Attack Works?
The man-in-the-middle attack is performed when the attacker gains complete control over the networking router along a normal flow of traffic. The cybercriminal, in most cases, is in the same broadcast domain as the victim. For example, a TCP connection exists between the server and client in an HTTP session. The MITM splits the link into two – one between the server and attacker and other between the victim and attacker. By interrupting the TCP connection, the attacker decodes, alters and inserts fake data into the communication. A man-in-the-middle attack aims to exploit the weaknesses in the communication protocol, convincing the source network to divert traffic through the attacker’s router.
Tips To Prevent Man-In-The-Middle Attacks
- Pay Attention To Certificate Warnings: A security certificate warning appearing for a website might indicate a serious problem. If the certificate doesn’t match with the server, you might be communicating with a malicious server carrying out a man-in-the-middle attack. Thus, you must not visit such websites, specifically if it involves entering important information like user names, passwords, bank account details etc.
- Check for HTTPS Encryption: When connecting to sites that process financial transactions such as online shopping or banking, make sure that the session has an HTTPS encryption. When communicating over HTTPS, your web browser checks identity certificates to confirm the credibility of the servers you are connecting to, thus, reducing the possibility of a phishing server.
- Be Careful While Using Wi-Fi Networks: Avoid doing any online transaction or sharing sensitive information if you are using a public Wi-Fi network. Be more alert if you see certificate warnings and websites without HTTPS encryption on such networks. Always try to use a private virtual private network (VPN) to create a secure connection to a trusted server.
- Install Anti-Virus Software: Installing and regularly updating anti-virus software can help you defend against man-in-the-middle attacks that involve infecting your computer with a malware.
We, at Centex Technologies provide the most advanced cyber security solutions for businesses. For more information, you can call us at (855) 375 – 9654.
