 PDF Version: Tokenization and Encryption
PDF Version: Tokenization and Encryption
Tag: Data Security Types
Data security refers to a set of standards, protocols, and techniques that are focused on protecting personal or organizational data from intentional or accidental destruction, modification, and disclosure. Different technologies and techniques can be applied to ensure data security. These techniques include administrative controls, physical security, logical controls, organizational standards, etc.
In order to choose the right data security protocols, it is important to understand different types of data security.
Authentication: It is the process of validating a registered user’s identity before allowing access to protected data. It is used in conjunction with authorization; the process of validating that the authenticated user has been granted permission to access the requested resources. Authentication involves a combination of ways to identify a user, such as passwords, PINS, security tokens, a swipe card, or biometrics.
Access Control: Authentication and authorization happen through access control. It is a method of guaranteeing that users are whom they say they are and that they have the appropriate access. Access control systems can include-
- Discretionary Access Control (DAC) assigns access rights based on user-specified rules.
- Mandatory Access Control (MAC) assigns user access based on information clearance.
- Role Based Access Control (RBAC) grants user access based on the user’s role and implements key security principles such as ‘least privilege’ and ‘separation of privilege’.
- Attribute Based Access Control (ABAC) assigns a series of attributes to each resource and user. The user’s attributes such as time of day, position, location, etc. are assessed to make a decision on access to the resource.
Backups & Recovery: An efficient data security strategy requires a plan for how to access the organization’s data in the event of system failure, disaster, data corruption, or data breach. This puts an emphasis on regular data backups. It involves making a copy of the data and storing it off-site or in the cloud. Also, it is important to formulate proper recovery protocols.
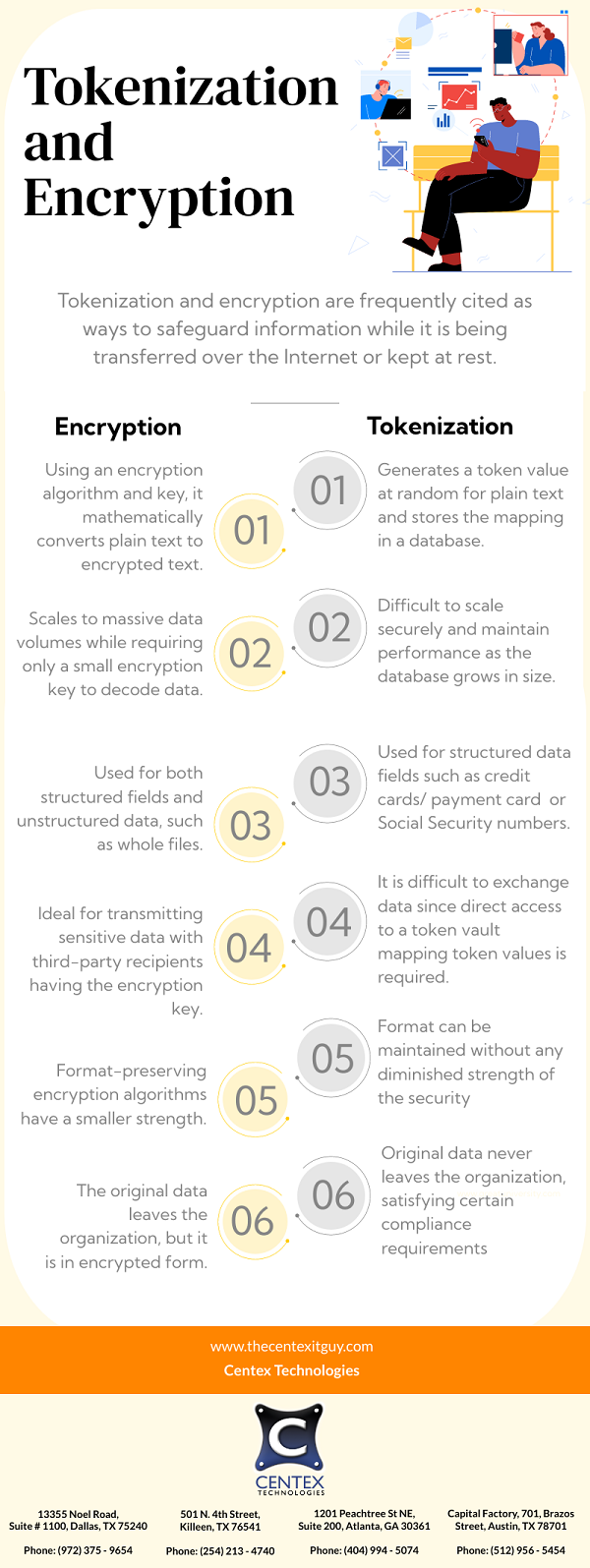
Encryption: Data encryption involves the translation of data into another form, or code so that it is accessible only by the authorized personnel who have the decryption key. However, it is highly important to ensure the security of decryption keys, critical management systems, and off-site encryption backup.
Data Masking: This type of data security involves the masking of original data by obscuring letters or numbers with proxy characters. The data is changed back to its original form by software only when it is received by an authorized user.
Tokenization: In this case, sensitive data is substituted with random characters that cannot be reversed. The relationship between data and its token values is stored in a protected database lookup table.
For more information on types of data security, contact Centex Technologies at (254) 213 – 4740.
