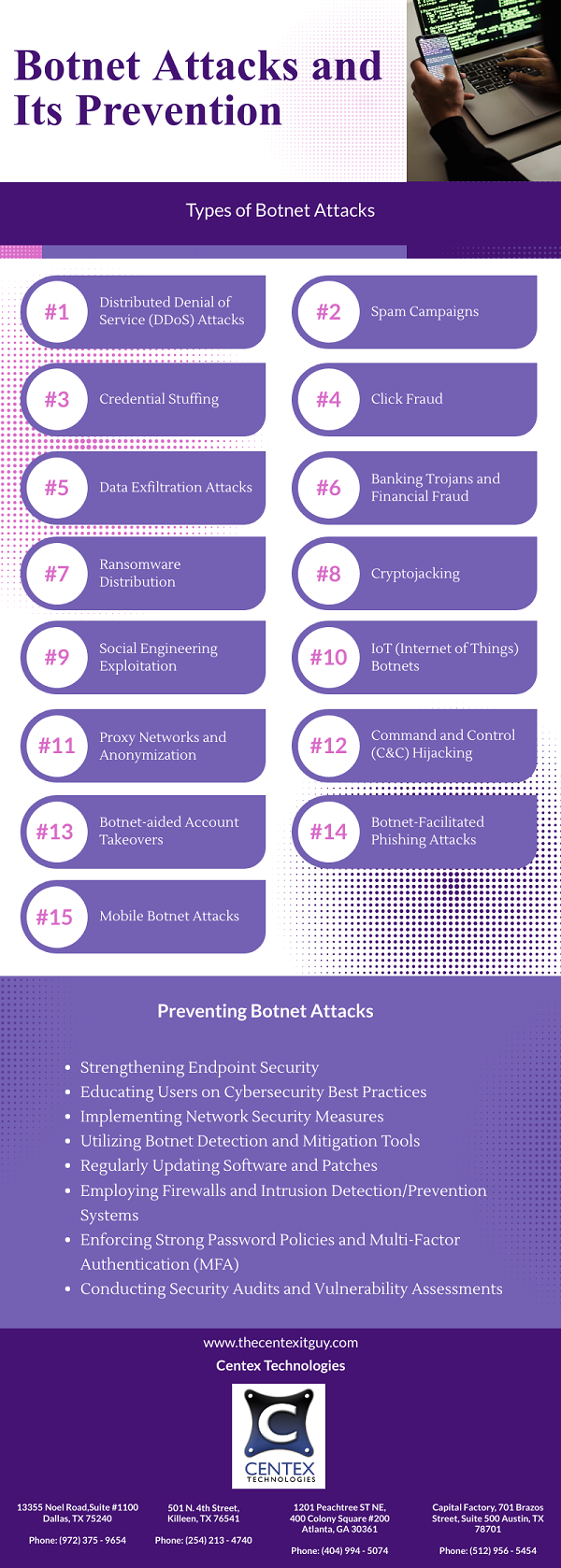
As the new school year approaches, students and educators are preparing for another year of learning, growth, and exploration. Technology has firmly established itself as a fundamental pillar in the education system, providing students with avenues for online research, collaborative endeavors, and distance learning. However, these advantages are accompanied by potential vulnerabilities related to cyber threats and breaches. To ensure a secure and productive academic year, it is crucial to prioritize cybersecurity. Here are some essential cybersecurity tips to consider as schools start anew.
Securing Credentials
Educating students, teachers, and staff to create strong and unique passwords is the first step in protecting against cyberattacks. It’s important for each account to have its own special password. Don’t use the same password on different websites. A good password usually has a mix of big and small letters, numbers, and symbols. Strong passwords make it harder for bad actors to get in.
Use Of Multi-Factor Authentication (MFA)
Implementing multi-factor authentication adds an extra layer of security to accounts. MFA requires users to provide two or more forms of verification before accessing an account. This could include a password or a code sent to their phone or biometric data like fingerprints or facial recognition. MFA significantly reduces the chances of unauthorized access even if a password is compromised.
Regularly Updating Software
Keeping software, including operating systems, browsers, and applications, up to date is essential. Software updates often contain patches for security vulnerabilities that hackers might exploit. Schools should establish a regular update schedule to ensure that all devices are running the latest versions of their software.
Secure Wi-Fi Networks
Secure Wi-Fi networks are critical to preventing unauthorized access. Schools should set up strong and encrypted Wi-Fi networks using WPA3 encryption. They should also avoid using easily guessable passwords for Wi-Fi access. Educators and students should be educated about the risks of connecting to public or unsecured networks, as these can expose devices to potential threats.
Educate Students and Staff
Cybersecurity education is paramount. Schools should conduct regular training sessions for students and staff to raise awareness about phishing emails, social engineering attacks, and safe online practices. Students should be taught how to identify suspicious emails, links, and attachments. Creating a culture of cybersecurity awareness can empower everyone to be vigilant against potential threats.
Data Privacy and Protection
Educational institutions manage confidential data related to students and staff, making data privacy and protection a top priority. Employing effective data encryption and access management controls ensures that only authorized individuals can access sensitive data. Schools should establish well-defined strategies for responding to data breaches, aiming to reduce the repercussions of any possible security incidents.
Safe Online Behavior
Promoting safe online behavior among students is crucial. This includes educating them on responsible usage of social media, emphasizing the significance of refraining from sharing personal information on the internet, and enlightening them about the potential repercussions of engaging in cyberbullying. Encourage students to think before they click and to report any suspicious online activity.
Keeping Regular Backups
Regularly backing up data is a fundamental cybersecurity practice. In the event of a ransomware attack or data loss, having up-to-date backups ensures that critical information can be restored without paying a ransom. Schools should schedule automated backups and store copies in secure off-site locations.
Mobile Device Security
Many students and teachers use mobile devices for learning and communication. It’s essential to secure these devices with strong passwords or biometric authentication.
Cybersecurity Policies and Incident Response
It’s important for schools to create well-defined cybersecurity policies that lay out the guidelines for how devices are used, how data is managed, and how people should behave online. These rules need to be clearly communicated to students, teachers, and staff. Additionally, schools should also create a detailed plan for how to respond to any potential cybersecurity issues that might arise.
For more information on cybersecurity solutions and best practices, contact Centex Technologies at Killeen (254) 213 – 4740, Dallas (972) 375 – 9654, Atlanta (404) 994 – 5074, and Austin (512) 956 – 5454