Tag: Cyber Security Page 23 of 41
SamSam is a targeted ransomware attack which incorporates custom infection using a wide range of exploits or brute force tactics. The ransomware is also known as Samas or SamsamCrypt. The first version of the ransomware was released in late 2015. The SamSam ransomware attacks do not make use of phishing or malware downloads to infect a network; instead they utilize following modes of infection:
- Vulnerabilities in Remote Desktop Protocols (RDP)
- Vulnerabilities in Java based web servers
- Vulnerabilities in File Transfer Protocol (FTP)
- Brute force against weak passwords
- Stolen login credentials
Once, the ransomware has initial foothold on the victim’s network, it compromises the network to gain control. Also, SamSam is a manual attack. Thus, in case an application detects the ransomware, the attackers modify a registry entry to disable the endpoint tool’s detection. This enables them to compromise the application and control the network. SamSam uses a number of applications to accomplish the attack such as Mimikatz, reGeorg, PsExec, PsInfo, RDPWrap, NLBrute, Impacket, CSVDE, PowerSploit and JexBoss.
During the reconnaissance phase, the attackers try to write a plain text file named test.txt to target. If successful, they add the target to a list titled alive.txt on Domain Controller (DC). After ensuring that DC has writing privileges for machines, the ransomware is deployed and pushed to all the machines controlled by DC simultaneously.
The ransomware follows an efficient approach for encrypting the files on infected machines.
- The encryption is initiated on holidays, weekends or late nights to buy time for maximizing the impact before getting noticed.
- Files with selective extensions or important files required for running the machines are encrypted first.
- The remaining applications or files are encrypted later; starting from smaller files and gradually moving towards larger files.
- A unique AES key is generated for every encrypted file.
- As soon as encryption is complete, ransomware deletes its installer and removes any traces of the attack.
- It becomes difficult for victims to download files from off shore backup because the applications required to run the machine are also inaccessible. Thus, they are required to go thorough time consuming process of reloading the disk and installing applications before downloading back up files.
A ransom note is left on target organization’s machines demanding a set amount of bitcoin currency to decrypt a single machine and a lump sum amount for decrypting all the machines at once. Every victim is provided a unique web address on dark web which leads to chat feature for communicating with the attackers. The chat is deleted after a victim pays the ransom.
Security Practices To Prevent SamSam Attack:
- Regularly install available patches for RDP service. Also, disable the service when not needed by the users.
- Ensure that no RDP ports are left open during interactions between cloud-based virtual machines and public IPs. If it is required to leave RDP Port of a system open, keep the system behind firewall and instruct users to communicate with this machine via VPN.
- Enable, two-factor authentication, strong passwords and account lockout policies.
For more information on how to secure your network, call Centex Technologies at (254) 213 – 4740.
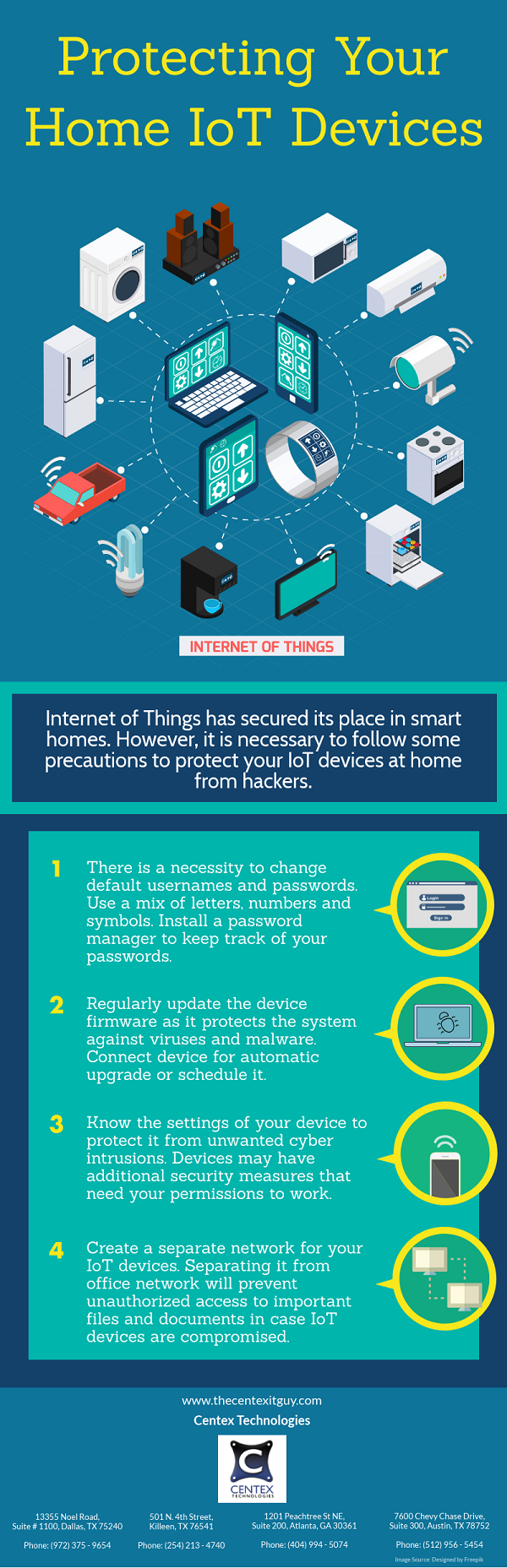
Though most of the businesses follow the basic IT security protocols like using strong passwords, installing updated security solutions and blocking unauthorized access; there is a constant increase in number of hacking instances. Nowadays, hackers utilize diverse mediums to serve as an entry points to infect a system or network and initiate widespread attacks. It is important to be aware of these entry points in order to develop effective cybersecurity strategies.
- Off-brand Apps: Some apps may not be available on certain operating systems. Hackers design off-brand apps with similar features and offer them for download on these operating systems. Once a user installs this app, the system is compromised and hackers gain access to his personal data like login details, photos, videos, etc. An example of such attack is the phishing attack that targeted Snapchat users. Hackers sent a link to users via a compromised account. This link pointed to a mobile site that was designed to look like Snapchat login page. As the users entered their login information, the details were copied and saved by the hackers. The stolen login information including passwords of affected users was then publicly posted on a phishing site.
- Home Appliances: Hackers now use home appliances like smart refrigerators to launch an attack. The smart home devices are generally factory configured including a preset password. It is common for users to forget to reset or personalize their password which makes them an easy target for hackers.
- Your Car: Most cars are installed with wireless or Bluetooth connectivity. The system enables users to enjoy benefits like keyless entries, remote start, navigation, etc. These features collect data like locations saved in navigation system, location where car is parked and other such vulnerable data. Car manufacturers tie up with third party data storage companies to store this personal information of users. This provides an opportunity for hackers to breach the system and steal the data.
- Cash Register: Hackers steal payment card details of customers by using POS Malware. When a card is swiped to make the payment, the payment card data is encrypted. The data is then decrypted in RAM of processing device to complete the payment. POS Malware attacks inefficiently secured systems to steal the payment card details from their RAM. The unencrypted data is then sent to the hacker. Stolen card details are then sold by the hackers.
- Fax Machine: The communication protocols of fax machines offer security vulnerabilities that can be used as loopholes by the hackers to launch widespread cyberattacks in organizations. Hackers create a colored jpeg image file coded with any type of malware. The coded image is sent to a target fax device where the image is decoded and saved into fax-printer’s memory. The malware can now spread over any network to which the fax printer is connected.
For more information about cybersecurity risks, call Centex Technologies at (254) 213 – 4740.
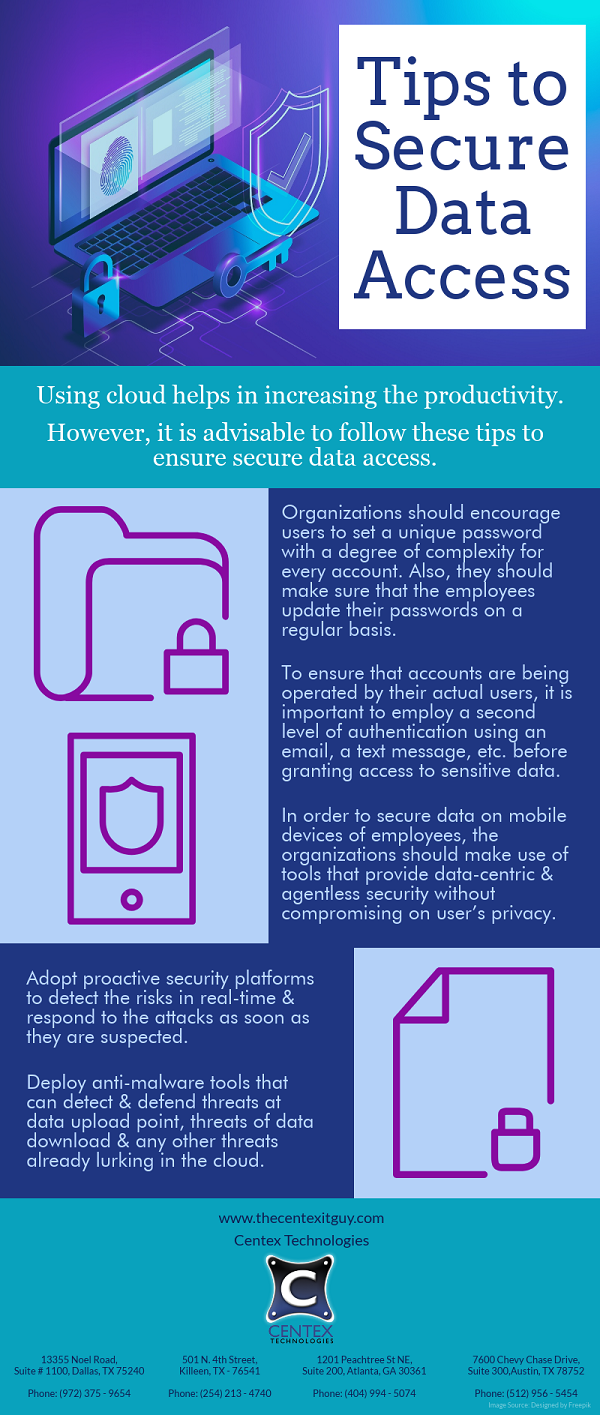
PDF Version: Tips-to-Secure-Data-Access
VPA (Virtual Personal Assistant) software application follow commands of a user intelligently and performs a variety of tasks such as searching information on the web, scheduling an appointment, monitoring health data, initiating online shopping, searching for addresses & location, etc. Also known as Intelligent Personal Assistant (IPAs); Siri, Google Now, Alexa, Cortana, etc. are the most commonly used ones.
Although Virtual Personal Assistants are of great use, there are certain security risks concerning them. Here we have discussed the most prominent security threats associated with VPAs
- Eavesdropping: A VPA is programmed to follow voice commands. So, it passively listens to everything being said, if the user forgets to turn it off when not in use. Thus, it ends up collecting user’s voice data without his knowledge. This recorded data always poses a risk of hijacking because cybercriminals might collect & use it unlawfully.
- Vast Exposure Of Personal Information: VPAs resort to different databases on the web in order to respond to user’s query. Although it is highly convenient, it can pose a serious security threat.
- Data Theft: VPA keeps a track of the user’s activity and stores that information on the device as well as a remote database. When an VPA hijacker gets hold of this information, he can extract the data and exploit it to offend the user.
- Voice/Audio Hijacking: This technology recognizes voice to take commands. Even though it understands different words & their pronunciations, it does not distinguish the voices of different users. This can be used against the user, as an impersonator might command the VPA to perform tasks that may harm the user. Even if it recognizes the user’s voice, there is a possibility that a cybercriminal might use the actual user’s voice recording and issue commands to the VPA.
- Remote Malware Downloading: A compromised VPA might be instructed to visit certain sites containing a malicious link. Once clicked, this link installs a malware in the device which continues to operate & damage the device remotely without the user’s knowledge.
- Undertake Tasks Autonomously: Users might register automated commands with a VPA. This can be exploited by the hijacker to victimize the user. For example, the user may direct his VPA to pay his phone bill every month. The VPA further takes the command and connects it to an authorized payment gateway. If the VPA is compromised, the hacker might dismiss the bill payment and transfer funds to his remote account.
There is no denying the fact that virtual personal assistants provide numerous benefits. However, it is important to stay cautious in order to avoid security risks.
For more information about IT, call Centex Technologies at (254) 213-4740.