PDF Version: Cybersecurity-Compliance-What-Is-It-and-How-To-Implement-It
Tag: Cyber Security Attack
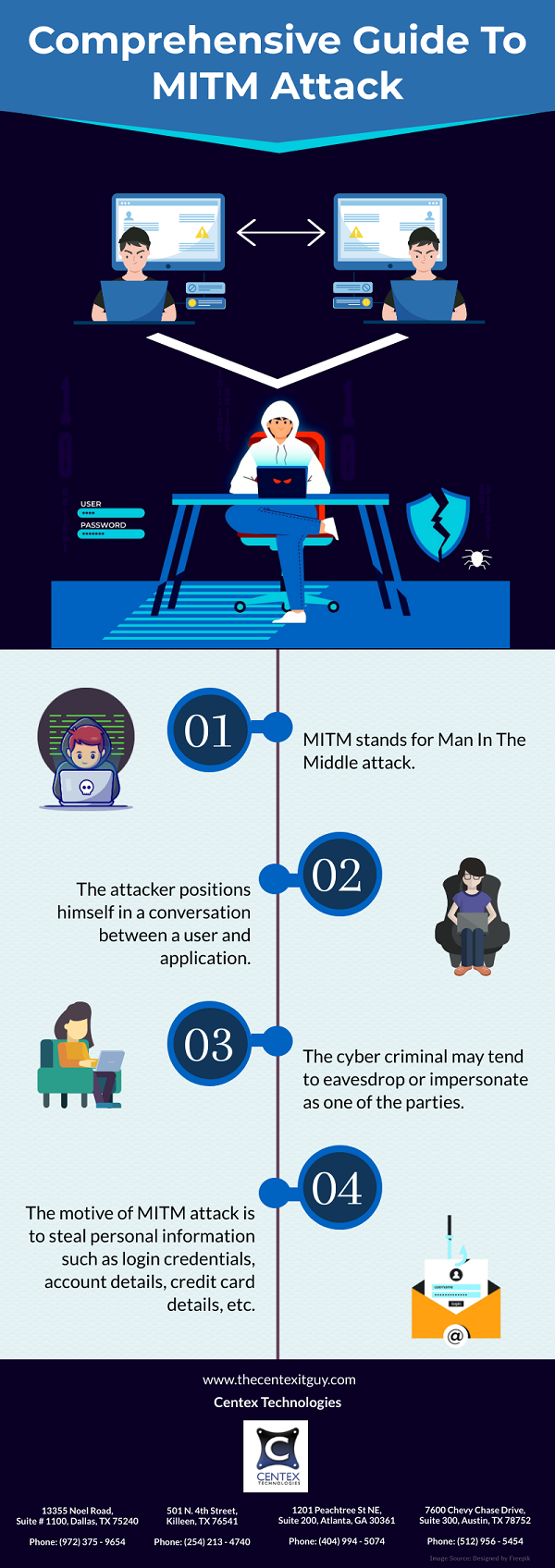
The following is a list of the top 50 cyber security terms that everyone should be familiar with: –
- Adware: Application or software displaying unsolicited advertisements on your devices.
- APT (Advanced Persistent Threat): Unauthorized user attacks and gains access to network or systems without being detected.
- Anti-Virus Software: Application program used to prevent, detect, mitigate and remediate malware.
- Authentication: A process ensuring, confirming, and verifying a user’s identity credentials.
- Back door: Secret method to bypass security and gain access to a restricted part of a network/system.
- Backup: To make copies of data stored on devices so as to reduce the potential impact of data loss.
- Baiting: Online baiting is facilitated by trapping any victim with fake incentives and profits/gains.
- Blackhat Hacker: Infringes laws and breaches computer security unethically for malicious purposes.
- Botnet: A group of internet-connected systems, including computers, servers, IoT, and mobile devices which are infected and controlled by a common malicious software operated by any blackhat hacker.
- Brute Force Attack: Repetitive successive attempts of various credential combinations.
- Bug: Error, fault, or flaw in an algorithm or a program resulting in unintended execution/behavior.
- Clickjacking: UI redressing attack creating invisible HTML page element overlaying the legitimate page.
- Cookie: Websites recognize users and devices keeping track of their preferences via stored cookies.
- Critical Update: A resolution software to address and resolve a high severity issue.
- Cyber Warfare: Cyber-attacks perpetrated by one digital entity against one/multiple other digital entities.
- Data Breach: A high-severity and a high-impact confirmed incident where a system or network data has been stolen without the consent and knowledge or authorization of the system’s or network’s owner.
- DDoS (Distributed Denial Of Service): A cyberattack aiming to disrupt an ongoing service by flooding it with malicious traffic from multiple sources or botnets affecting the availability of that service online.
- Deepfake: Videos that have human faces either swapped or morphed, leveraging AI algorithms.
- Exploit: Malicious code or script used to target vulnerabilities in systems and networks.
- Honeypots: Decoy networks or systems operationalized to lure potential attackers.
- Incident Response Policy: A plan stating the company’s response to any cyber security incident.
- Keystroke Logger: Software covertly logging the keyboard and mouse keys pressed/clicked in devices.
- Malware: Malicious software developed to cause damage to any target device or network.
- Malvertising: Using online advertisements and allied print management services to deliver malware.
- MFA (Multi-Factor Authentication): A security process where a user provides multiple authentication factors to identify themselves.
- Packet Sniffer: Software designed to monitor and record network traffic.
- Patch: A code applied after the software program has been installed to rectify an issue in that program.
- Penetration testing: Pentesting is the science of testing not only networks and systems but also websites and software to find vulnerabilities that an attacker could exploit.
- Phishing: Method to try and gather PII (Personally Identifiable Information) using deceptive emails.
- Pre-texting: Act of creating fictional narratives manipulating victims into disclosing sensitive information.
- Ransomware: Malicious software deployed to block access to devices until a sum of money is paid.
- Rootkit: A type of malware developed to stay hidden and persistent inside the hardware of devices.
- Security Awareness Training: Program aimed to improve end-user security awareness of employees.
- SOC (Security Operations Centre): Monitors digital activities to prevent, detect, mitigate and respond to any potential threats, risks, and vulnerabilities.
- Smishing: A type of phishing involving text messages to lure victims.
- Social Engineering: The art and science of manipulating people to disclose confidential information.
- Spear Phishing: Email-spoofing attack targetting a specific organization or individual to obtain PII data.
- Spyware: A type of software installing itself on devices to secretly monitor and report victims’ activities.
- Tailgating: Someone lacking proper authentication follows a legitimate employee into a restricted area.
- Trojan: Malicious software disguised as legitimate software to gain access to systems of target users.
- 2FA: A security process where a user provides two authentication factors to identify themselves.
- Virus: Malicious program on devices performing malicious activities without user’s knowledge & consent.
- Virtual Private Network (VPN): A software allowing users to stay anonymous while using internet services by masking/hiding their real location and encrypting communications traffic.
- Vulnerability: A vulnerability refers to a flaw in a system that can leave it open to attack.
- Vishing: A form of phishing to scam victims over the phone to gather PII data used for identity theft.
- Whaling: A type of phishing targeted at specific high-profile company leadership and management.
- Whitehat Hacker: Perform ethical hacking on behalf of legitimate entities and organizations.
- Worm: Computer program replicating itself to spread to other devices in the network.
- Zero-Day: A recently discovered vulnerability that hackers are using to breach into networks & systems.
Contact Centex Technologies at (254) 213 – 4740. for IT and Cybersecurity Solutions for businesses.
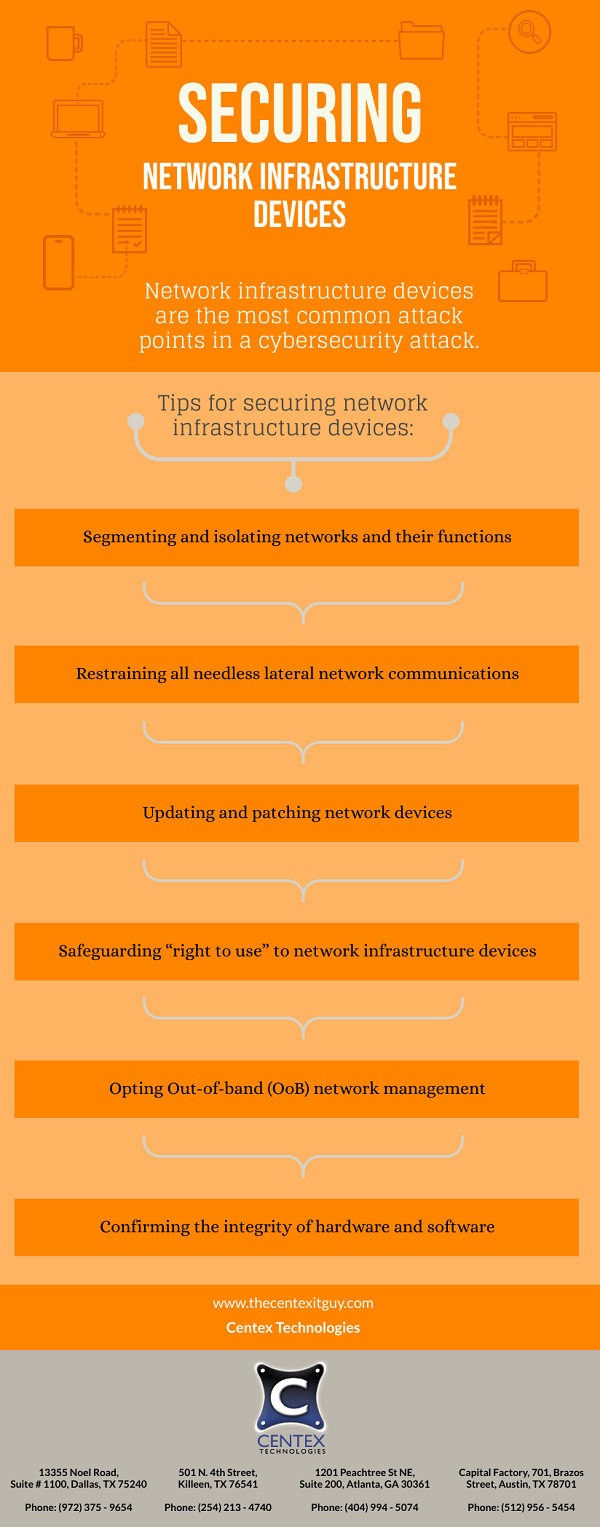
With advanced methods of cybersecurity attacks and breaches coming into play, business organizations need to be more vigilant in planning their course of action to ensure their safety. This is where the need for cybersecurity strategy & implementation plan arises.
What Is Cybersecurity Strategy & Implementation Plan (CSIP)?
CSIP is a plan that states the steps to be taken for formulation, implementation, testing, and refining an efficient strategy to secure an organization against cybersecurity attacks. The intent of CSIP is to identify & address critical cybersecurity gaps and emerging priorities.
What Are The Objectives Of Cybersecurity Strategy & Implementation Plan?
There are five main objectives of CSIP, namely:
- Prioritized Identification & Protection: This involves analysis of organizational resources to form separate categories of data, information, and resources. These categories are then prioritized based on their value. This helps in identification of high value information & assets that need to be secured immediately. After identification, it is important to understand types of risks against the identified assets such as outsider risks (network breach, phishing, hacking, etc.) or insider threats (rogue employees, unaware employees, compromised flash drives, etc.). The detection of risks makes it easier to define the strategic steps to protect the assets. Test your strategy & refine it. Once top priority information is secured, repeat the process for category of assets at next priority level.
- Timely Detection & Rapid Response: Cyber criminals keep evolving their attacks to disrupt stringent cybersecurity strategies. If not detected timely, these attacks can disrupt the layers of security to reach core network, data center and systems of an organization. So, conduct regular checks and analysis to detect a cybersecurity disruption at its nascent stage and stage a rapid response against it. Also, train the employees to make them capable of spotting a cybersecurity breach.
- Rapid Recovery: Some security breaches may cause damage; however, a rapid recovery can help in containing the widespread of damage. It is important to formulate rapid recovery plan. The plan should include steps to be taken, role of teams & individual employees in recovery, and security checkups to ensure the threat has been nullified.
- Skill Building: Recruit qualified cybersecurity workforce to stay protected. An alternative approach is to seek services of a cybersecurity firm and invest in SaaS applications. Conduct regular trainings to enhance cybersecurity knowledge and skills of all employees. This will help them in staying protected against individual targeting attacks such as phishing.
- Technology: Focus on efficient & effective acquisition and deployment of existing & emerging technology. Make sure all systems and devices are updated with latest software & security patches.
For more information on cybersecurity strategy & implementation plan, contact Centex Technologies at (254) 213 – 4740.