Tag: WiFi
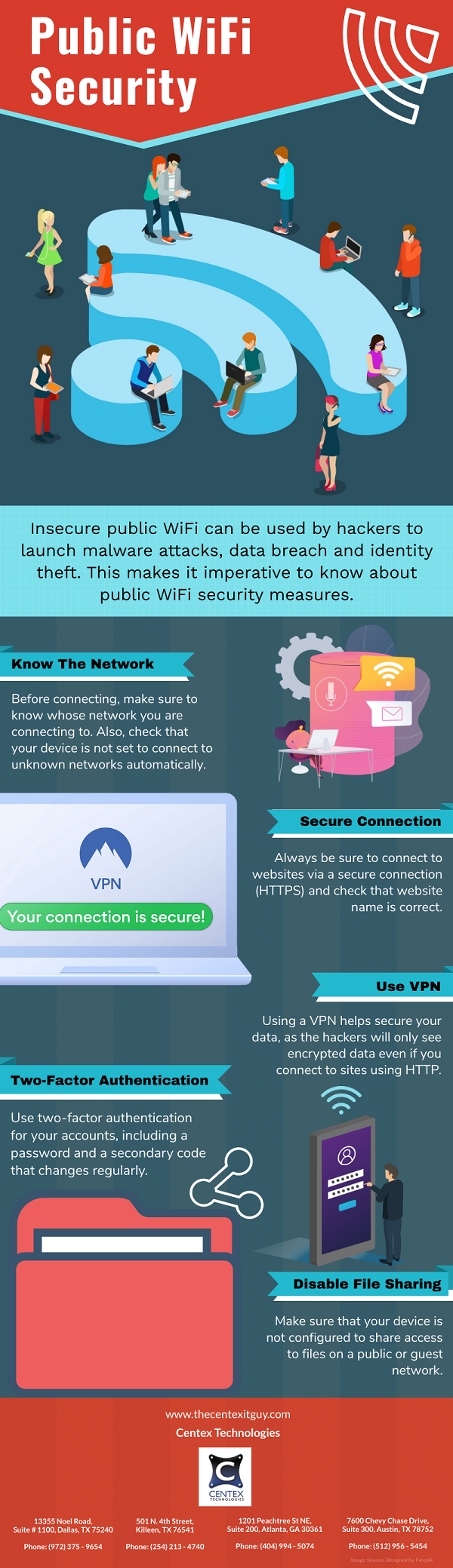 PDF Version: Public-WiFi-Security
PDF Version: Public-WiFi-Security
With the advancement of technology, there has been a rise in the use of wireless connectivity solutions. It has found applications in restaurants, coffee shops, offices and shopping malls. However, wireless connectivity in the form of Wi-Fi is inherently less secure. It is largely unprotected from threats that can result in theft of credentials and sensitive information. The unprotected access points expose your connection and personal data to cyber-attacks such as ‘Evil Twin Attack’.
Understanding An Evil Twin
An evil twin is a rogue wireless access point that appears as a genuine hotspot offered by a legitimate provider. It typically clones the MAC address, name and service set identifier (SSID) of the network. This makes it hard for the users to differentiate between original and fake access point.
An attacker can conveniently create an “evil twin” within the smart phone or other internet-capable device using some easily available software. He discovers the radio frequency of a legitimate access point and uses the same to send out his own radio signals with the same name as original access point. This enables the attacker to eavesdrop on the network traffic, capture traffic or plant malware on the system.
Implications To Cybersecurity
Once the fake access point is set up, it poses as a local hotspot. The attacker positions himself near the end-user so that his signal is strongest within the range. The strong signals tempt users to connect manually to the evil twin for internet access. Also, it can be a case where the end-user’s computer automatically chooses that connection. This allows the hacker to intercept user’s sensitive data that is being shared between user and the host. Thus, he can obtain sensitive information or login credentials resulting in identity theft or financial loss of the end-user. Attackers are also using social engineering to clone a login page through which credentials can be stolen.
Ways To Prevent Evil Twin Attack
To avoid evil twin network connections, following tips should be considered by end-users:
- Refrain from using public hot spots for online shopping or banking.
- Users should disable auto connect feature on all wireless devices.
- Connect via a virtual private network (VPN) to compress all traffic while using a public access point.
- Before connecting, ask the owner of the area for official name of the hotspot and security key, if any. Type the incorrect key intentionally; evil twin hotspots will grant access irrespective of the key.
Companies should also incorporate measures to protect corporate data from evil twin attack:
- Instruct employees to use Wi-Fi Intrusion Prevention Systems (WIPS) to prevent their systems from connecting to unauthorized duplicate access points.
- Protect company’s wireless connections with Personal Security Key (PSK) and provide its details to employees and customers.
For more information on IT security solutions for your business, call Centex Technologies at (254) 213 – 4740.
August 17, 2011
The use of wireless internet technologies for surfing various web pages has been increasing for a long time due to the ease and convenience that it offers to users. People are no longer sticking to fixed broadband lines connected to a fixed operating system and are instead accessing the internet through portable devices like laptops, tablets, phones, etc. Many places these days we have wi-fi connections that can be accessed by procuring the requisite username and password from the owners either by paying a certain fee or even free of cost in some cases.
This kind of free access to the internet at public places is making web surfers more prone to virus attacks that may be made through the openness offered by wireless internet systems. Anyone in the vicinity who is able to receive the wi-fi signal can simply log on to the network especially if it is being offered free of cost. In such a network, there can be all kinds of security lapses that may put your system at the receiving end of virus attacks. There are some tips mentioned below to help you avoid such attacks or at least help reduce their incidence:
- Before logging onto any kind of free internet at a public place, you should ensure that the network is protected by the required firewall and antivirus software so as to build a multi protected layer for your operating system. There should be a strong IT department taking care of such requirements. You should beware of connecting your laptop the internet in the vicinity without checking for security problems that the internet may have.
- It is advisable not to access websites and fill in your username and password at sites that contain private information about you that if stolen, may pose a significant threat to you. You should refrain from opening bank related websites or shopping websites where you need to fill in credit card related information.
- It is essential to have good antivirus software installed on your operating system to help ward off virus attacks. Although not completely fool proof, such software can help reduce the number of attacks that your system may be subjected to.
For complete system and network protection tips, feel free to contact us at Centex Technologies. We serve Central Texas including Killeen, Austin and Dallas.


