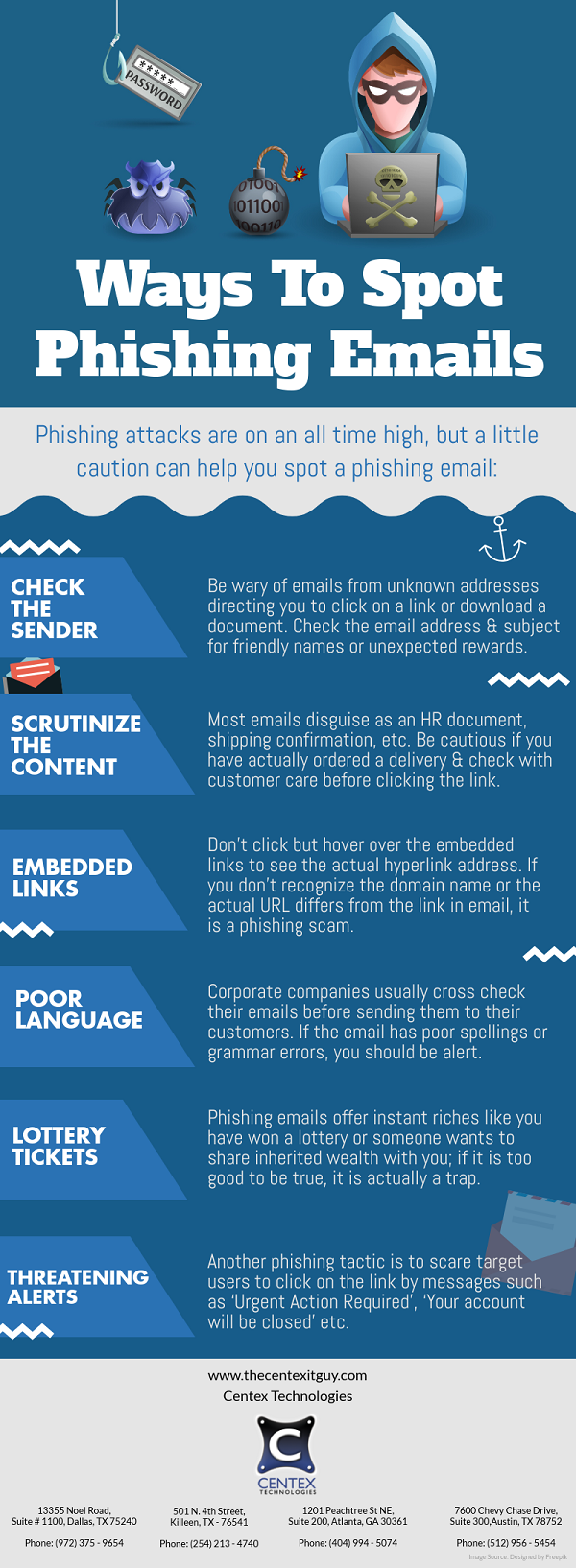
With continuous growth in the number of cyber-attacks, user authentication has become one of the most important aspects in information security. User authentication is accomplished through passwords that should be entered by a user in order to prove his identity and gain access to a computer or communication system. Traditionally, text based passwords are used for authentication. However, text passwords are highly vulnerable and pose as an easy target for hackers. Thus, modern authentication techniques based on graphical methods are now being used to combat hacking practices.
Graphical user authentication is an attractive alternative to alphanumeric passwords. To setup a password, the users have to select an image at a series of subsequent screens. The images are presented specifically in a graphical user interface. As a large number of pictures are presented at every screen; the number of possible combination of images is extensive. This offers better resistance to dictionary attacks as compared to text-based password approach. Also, the graphical password approach is considered to be more user friendly than a text based password.
Due to the advantages that graphical passwords offer, there is a growing usage of these in workstations and web log-in applications. Graphical passwords are also being applied to ATM machines and mobile devices.
Categories of graphical password techniques are:
- Recognition Based System: In this technique, the user is presented with a set of images and is challenged to identify a single or more images that were selected during the registration stage. The user has to identify the pre-selected images in order to be authenticated. Such recognition systems are also called search metric systems. To use graphical recognition schemes, the system is required to retain some information from user specific profile data. This helps the system to know which images belong to a user’s portfolio and display them at the time of login authentication.
- Recall Based System: In recall based techniques, the user is required to create a drawing to set up the password. The recall based passwords are typically drawn on a blank canvas or a grid. At the time of login, the user has to reproduce the drawing that he created during the registration process. These graphical based systems are referred to as draw metric systems because user authentication is based on using the drawn image as a reference.
Following are some points that should be considered before implementing a graphical password:
- The password contains image as a reference and encryption algorithm.
- The login contains username, images, graphical password and related methods.
- SSR shield for shoulder surfing.
- The grids contain unique grid values and grid clicking related methods.
For more information on graphical user authentication, call Centex Technologies at (254) 213 – 4740.