Businesses must protect themselves from the most advanced malware attacks by organized threat groups nicknamed by many cybersecurity vendors as APTs (Advanced Persistent Threats). Malicious programs and software propagated by APT groups are designed to break into computer systems and steal data. APT malware can be difficult to detect and often go undetected for long periods. Hackers often use it to gain access to confidential information.
How would security personnel know whether the organization has been attacked by an APT group?
Multiple signatures and behavioral changes indicate that organizational network infrastructure has possibly become a victim of an APT malware attack. Some of the common indications are as follows: –
- Unexplained or sudden changes in the behavior of computer systems or networks.
- Unauthorized access to or use of computer systems or networks.
- Unexpected or unexplained emails, attachments, or websites.
- Use of malicious software, such as viruses, worms, or Trojan horses.
- Suspicious or unauthorized network traffic or communications.
- Unusual patterns in file downloads or access.
- Changes in system configurations or settings.
- Suspicious or unauthorized use of privileged accounts.
- Tampering with or destruction of computer systems or data.
- The appearance of phishing or other social engineering attacks.
Advice for Security personnel to mitigate APT malware attacks
The most important thing is to have a plan before the attack. Security professionals need to have a plan for responding to the attack, recovering business-critical data, and preventing future attacks. SOCs (Security Operations Centers) should also have a backup and disaster recovery plan. All mission-critical data must be backed up regularly. There must be a plan in place to recover the corporate data if the primary systems or servers are damaged or destroyed. Security personnel is advised to follow the below-mentioned mitigation steps if the APT malware has infected the network systems of an organization:
- Disconnect all the corporate devices from the internet.
- Reboot those devices in safe mode.
- Run an anti-virus scan.
- Remove any infected files detected.
- Restart corporate devices in normal operating mode.
- Connect the devices to the internet.
- Run an anti-virus scan again.
- Remove any infected files detected.
- Now, restart the devices in safe mode.
- Run an anti-virus scan again.
- Remove any infected files detected.
How to proactively protect businesses and prevent APT malware attacks?
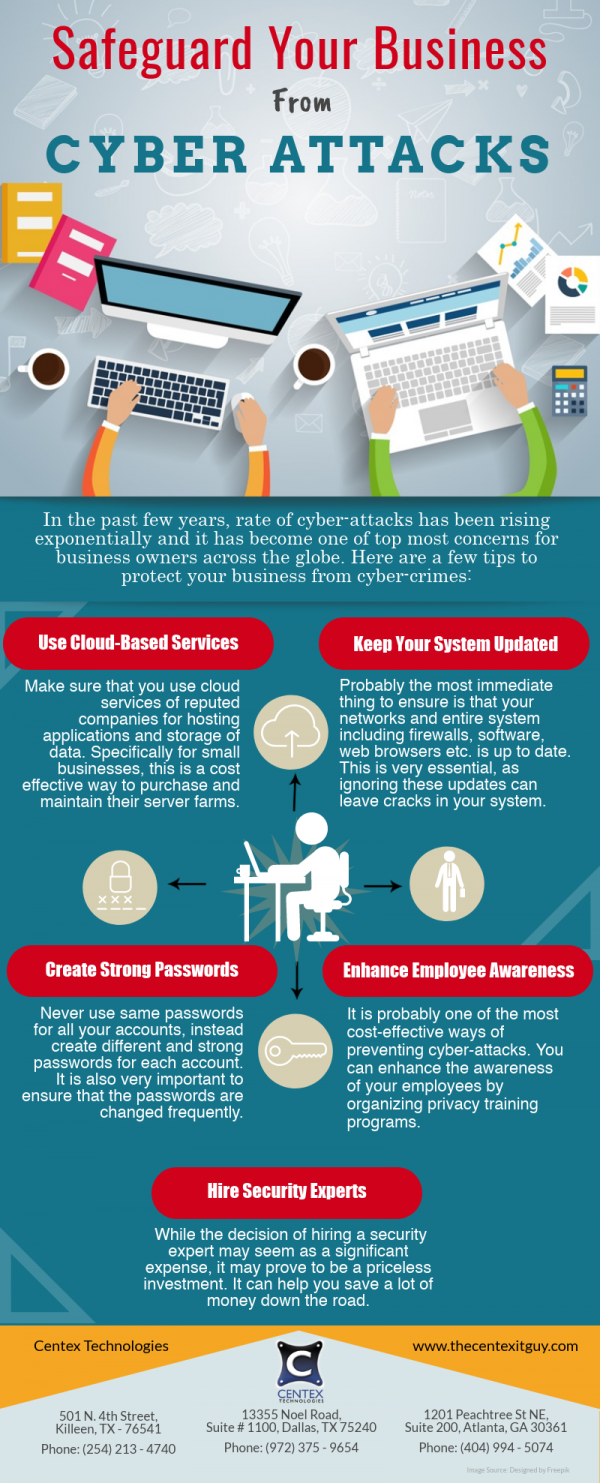
Businesses can follow several best practices to protect themselves from APT malware. One of the most important steps is to install up-to-date security software on all devices and to make sure that all software is regularly updated. Businesses should also create strong passwords and use multi-factor authentication whenever possible. It is also important to be aware of phishing attacks and to never open emails or attachments from unknown sources. Finally, businesses should regularly back up their data. Here are a few tips to help security professionals protect the business from APT malware:
- Keep the software solutions and applications up to date. The software upgrades must be regularly checked to ensure the software is patched to recently disclosed vulnerabilities. The operating systems and other security solutions must be upgraded to the officially supported maintenance version offered by the vendor.
- Deploying a network and a web application firewall can help protect your business from network-based malware attacks by blocking unwanted and malicious traffic.
- Using strong and unique passwords and credentials are of utmost importance and a basic security best practice. Employees are advised never to use the same credentials for multiple accounts.
- Ensuring employee and staff cyber security awareness and education programs help the employees become aware of the risks of APT malware. They must be trained to thwart such attacks.
- Back up data in DR (Disaster Recovery) servers that are off-site and located across different regions in the world. This can help protect corporate data in the event of data loss or a malware attack.
Cybersecurity strategies for business leaders
There are many ways in which businesses can protect themselves from APT malware. One of the best ways to prevent an APT attack is to have a comprehensive security plan in place. This security plan should include measures such as firewalls, anti-virus software, intrusion detection systems, and email security. Businesses should also keep their software up to date. Out-of-date software is more vulnerable to attack. Employees should also be educated about APT attacks. They should be aware of the signs of an attack and know what to do if they think they are being targeted. Businesses should also have an incident response plan in place. If they are attacked, they will need to know how to respond. This plan should include steps to take to secure the network and how to investigate the attack. Following the Defense-in-Depth approach, the security leadership can also take steps to proactively protect the network infrastructure from future cyberattacks. Leaders are advised to stay calm if they are hit by an APT malware attack. Attackers or cyber criminals take the advantage of unnecessary panic. Stay calm and take the necessary steps to recover the system and protect the data.
Centex Technologies provide cybersecurity and computer networking solutions. You can contact Centex Technologies at Killeen (254) 213 – 4740, Dallas (972) 375 – 9654, Atlanta (404) 994 – 5074, and Austin (512) 956 – 5454.